Cryptography was created by thinking about how to achieve secure communication. Person "A" wants to send a message to Person "B". How can "A" send a private message to "B" over an insecure channel? How to avoid someone non-authorized from reading it? A Man-In-The-Middle (MITM) is an attacker in the channel where "A" and "B" are transmitting information, impersonating both.
The attacker reading their messages (that is, compromising confidentiality) is not necessarily the worst thing that could happen. It could also use the trust of "B" in "A" to commit fraud. It could inject malware into the messages to compromise Alice and Bob's systems without them suspecting anything. The limit is the imagination.
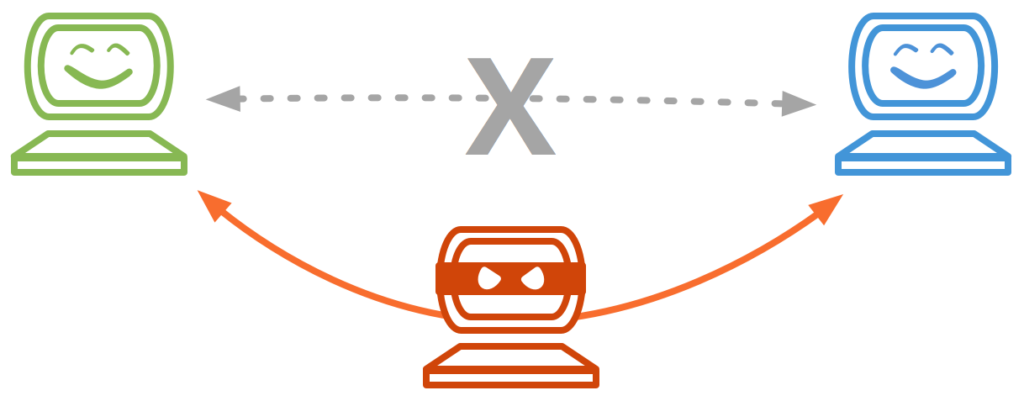
What is Man-In-The-Middle?
"A" and "B" are sending messages to each other in an ongoing MITM attack, believing they are communicating directly. But every message from both sides is arriving with the attacker, who controls the conversation and its content.
Source
Several remarkable examples of these attacks were perpetrated by big players targeting their own users. For example, in 2003, it was discovered that the popular router company, Belkin, was redirecting some of the users' HTTP traffic to their product's pages.
An even more worrying example involves a nation-state intelligence agency, the NSA. According to reports from 2013, they were "in the middle" between the giant Google and Users, gathering information.
Symptoms of MITM
- Higher latency:
The data passes by an additional middle point where an attacker can be encrypting, decrypting, injecting, etc., increasing the latency.
- Repeated and/or unexpected disconnections:
An attacker may force the connection to restart several times. This way, you would need to input your authentication data again so that it could be retrieved.
- Strange URLs in your browser:
An attacker may trick you into connecting to a site under its control.
For example, if the offender is between you and the Domain Name System (DNS), it may redirect your request attempt to "example.com" towards something that looks similar, like "exanple.com".
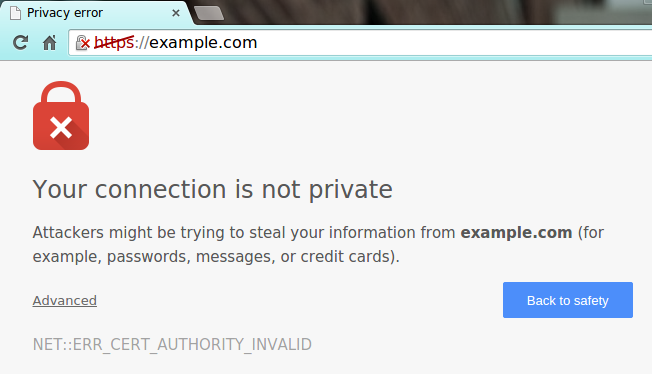
- Invalid Certificate Errors:
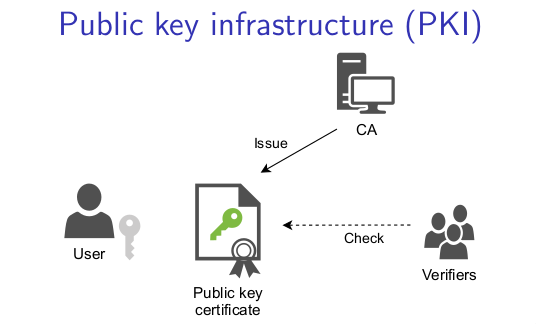
One way of preventing these attacks is by properly authenticating each endpoint.
For that, a Cryptographic structure named "Certificate" is used. Resuming, certificates link domains with identities via a trusted authority entity, which signs them.
If, for example, you try to browse a web page, and it sends a certificate that the authority signature is not in your browser's database, you will receive a warning about that, stating the party to which you are connecting has a non trusted certificate.
Source
Even though this is very useful to confirm you are connecting to the domain you want to, you still need to be careful.
Diginotar, a Dutch Certificates Authority, was breached in 2011. MITM attacks were performed using false certificates. These were not detectable as they had a valid authority signature.
Types of MITM
MITM attacks can happen anywhere.
For example, in your Local Area Network (LAN), between you and your router or another device.
Or even remotely when trying to access a server through a gateway.
It is usual to classify these attacks by the technologies and protocols involved. Some of the most commons are:
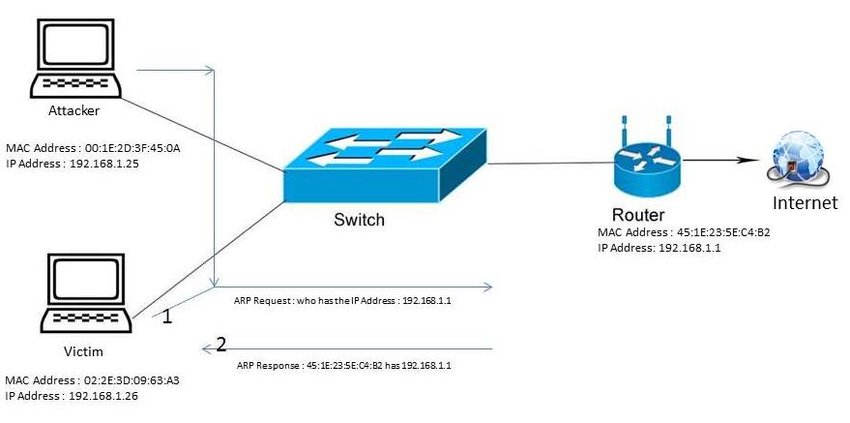
#1: ARP Poisoning
Source
Address Resolution Protocol (ARP) maps Media Access Control (MAC) addresses of the devices to IP addresses in a LAN.
- An attacker can flood you with specially crafted ARP packets, so you believe its IP is the gateway's IP.
- The attacker will flood the gateway with ARP packets, so it believes you are the sender.
- The packets sent to you by the gateway will arrive first to the attacker and the same in the opposite direction. The attacker can do whatever he or she wants with the packets before forwarding them to you or the gateway.
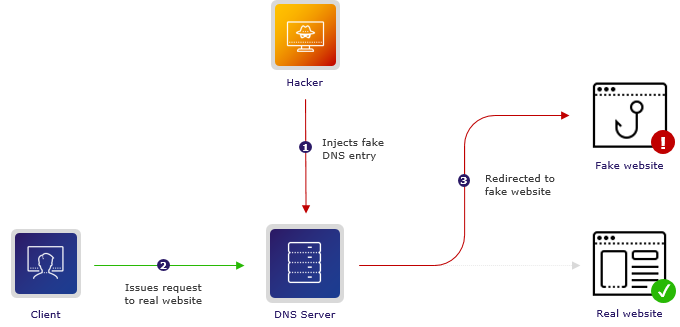
#2: DNS Cache Poisoning
Source
DNS translates domain and hostnames into IP addresses. If an attacker can "poison" your DNS table, by mapping a domain you want to browse with an IP under its control...you are in trouble.
Even worse, perhaps the attacker can trick you into using its own malicious DNS resolver. The above-mentioned can be achieved, for example, if the attacker can see your traffic and reply faster to your requests than your DNS. This risk is present in LAN networks when trying to connect to a remote host.
#3: HTTPS Spoofing
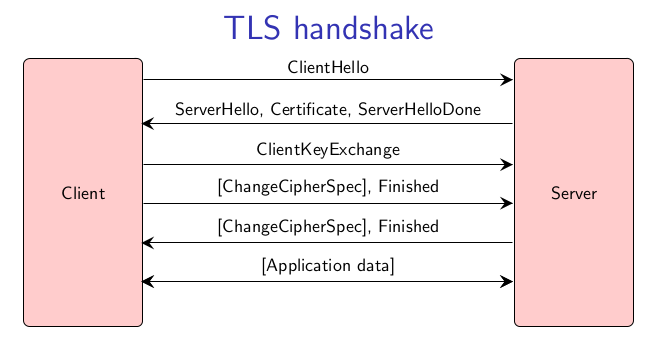
HTTP is the protocol used when browsing. The "S" in HTTPS stands for "secure" because it has an additional layer of cryptography aimed to encrypt and authenticate the communication between you and a server.
The cryptographic protocol used for that is named Transport Layer Security (TLS) which had in older versions the name Secure Sockets Layer (SSL).
However, even though HTTPS provides authentication, an attacker could trick you into connecting to a different website under its control with a similar name, as discussed in the previous section.
As MITM is an old-known; there exists plenty of tools and frameworks to perform these attacks. You can even find specialized tools for certain applications, like sniffing traffic, injecting, denying service, etc.
For example:
- Dsniff is a collection of tools for performing attacks on protocols ARP, DNS, HTTPS, SSH, and more. Some utilities come installed by default in popular pen-testing distros, like Kali Linux.
- Bettercap framework provides tools to perform MITM attacks in WIFI, Bluetooth Low Energy (BLE) networks, and similar.
For example, it provides the possibility of performing "Evil Twin Attack", which consists of creating a cloned fake access point to trick users to connect to retrieve their login credentials.
Source
Top MITM Attacks Statistics
As mentioned before, HTTPS is more secure than HTTP because it provides authentication and encryption. In fact, HTTP sends data in clear. That means anyone watching the network traffic can read and understand what was sent and received. This includes sensitive data, like your passwords.
When browsing, we usually input the addresses in the search bar without specifying the protocol http:// or https://. In these cases, the browser will default to insecure HTTP, which can make a non-encrypted connection or even allow an attacker to redirect our traffic to a page under their control.
To avoid that, it was created a security feature named HTTP Strict Transport Security (HSTS). It can be set in the HTTP packet header.
What does it do? If implemented, it will allow your browser to connect to a server if and only if it uses HTTPS protocol.
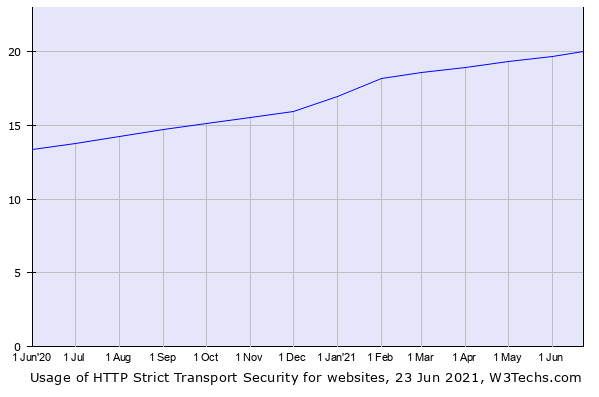
That is great! However, here comes the shocking fact. This feature is available in all modern browsers today, but it is implemented only by 20% of all Internet Websites. Even several banking websites lack it!
How can you defend against MITM Attacks?
To defend against this risk, you need to ensure the packets sent or received have not been tampered with on the way.
Also, you need to verify the identity of with whom you are communicating. The authenticity of each endpoint has to be checked. The best idea is to adopt a communication protocol with already built-in measures for integrity, and use it properly.
For example, for web browsing, HTTPS (with TLS Protocol under the hood) prevents tampering by sending hashes of all previous messages and authentication with a Public Key Infrastructure (PKI). The last is what we mentioned before related to Certificates and an Authority.
However, as we saw, this can be not enough. We should enforce the use of secure communications with HSTS, and check periodically that certificates are valid.
How can BitNinja protect against MITM Attacks?
If you are a victim of a MITM attack, the attacker will try to redirect you to malicious websites and/or install harmful files in your server to take control and/or retrieve sensitive information. This is when BitNinja can protect you as it knows best.
With innovative and unique techniques for Malware detection, BitNinja's "Structure Analysis" can detect malware in real-time, even if its code is obfuscated.
But not only that, BitNinja's "DefenseRobot" goes a step further to find the source of the infection, block the involved IPs, and apply Honeypot technologies to isolate the affected domains.
This last measure is especially helpful for avoiding deeper compromise of the affected systems and log information that can help catch the attackers.
Why is it different from other WAF solutions?
BitNinja Malware Detection Module's way of looking for threats is unique and patent-pending.
Custom Malware signatures are supported and easy to add.
BitNinja AI-powered Defense Robot Module automatically works to find the root cause of an infection.
When managing several HTTPS connections, the server can get overloaded with too many operations, like checking signatures, doing encryption, and decryption. BitNinja SSL Terminating Module allows Certificate Miners and offload HTTPS requests, enhancing the server stability and performance.
Example for MITM Attack
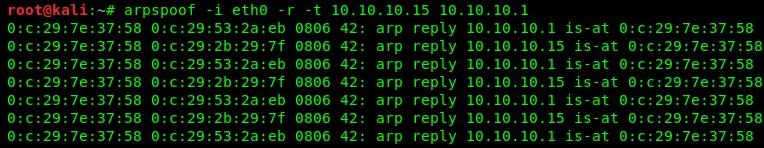
- An attacker in your LAN establishes a MITM position by using the popular utility "arpsoof":
- The attacker tries to redirect you to a malicious website under its control. If you are using BitNinja, and the website is in the Malware's database (which would be likely the case in a big-scale attack), nothing will happen to you. The connection will be denied, and you are safe.
- Even if the website happened not to be in the database, an attempt to install malware on your system would be blocked by BitNinja Malware Detection Module.
Man-In-The-Middle (MITM) FAQs
Why are MITM Attacks important to prevent?
A MITM attack is not in actual lists like OWASP Top 10, where you can find the Web Application Security Risks of major concern regarding consequences and statistics of last year's attacks. But the outcomes associated with a victorious MITM attack are so catastrophic that defenses come built-in for all the main communication protocols we use nowadays
How BitNinja protects against landing on a malicious website?
BitNinja counts with a crowd-sourced and constantly updated database of over 100 million IP Addresses. This is a unique asset in the market to enhance protection—even against zero-day attacks.
MITM attacks can compromise the confidentiality, integrity, and availability of important assets. Cybersecurity is not optional anymore. It is a must! If you haven't tried BitNinja yet, don't forget to register for the 7-day free trial! No credit card needed!
Free Trial
We are always happy to help you! If you have any questions, check out our Knowledgebase, feel free to ask at info@bitninja.io, or you can even reach us on the Dashboard chat!
Let's make the internet a safer place together!