Our team has attended the CloudFest back in March where during the security panel we have attended a presentation about the importance of security by design an important thing in terms of responsibility and suggested OWASP as a standard to start with. In this blog post we would like to show, why it is important for developers too, not just for security providers.
The best way to define it is an approach to software and hardware development where the main goal is to make a system as free of vulnerabilities and imprevious to attack as possible. To achieve this there is a need for a huge amount of continuous testing, authentication safeguards, and adherence to best programming practices.
Many things, especially input, should be distributed by a secure design.
Let's see an insecure design in practice:
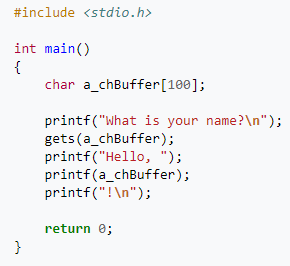
When designing you must consider the most likely attackers ( in order of likelihood) like :
- Annoyed staff
- Trojan attack
- Criminal attackers or organized crime
- Script kiddies
It is important to address any kind of existing vulnerability and patching the security holes as they are found can be a hit-and-miss process and will never be as effective.
The design principles, like privacy, the integrity, and availability - while they are important, wide and blurred - will not change. In the form of security architecture, the need for application security is as great as a construction of a building or a bridge.
We have to follow some principles in order to reach the goal :
Minimize attack surface area
The high-quality protection version can be applied to a number of specific software security regions. as an example, while performing enter validation, the fine version dictates which you have to specify the characteristics of enter with the intention to be allowed, as opposed to looking to filter terrible input.
Establish secure defaults
There are numerous ways to supply an “out of the box” enjoy for users. but, via default, the enjoy ought to be at ease. with the aid of default, the software ought to have integrity controls grew to become one.
Principle of Least privilege
The precept of least privilege recommends that accounts have the least quantity of privilege required to perform their business processes. This encompasses user rights, resource permissions consisting of CPU limits, memory, network, and file system permissions.
Principle of Defense in depth
The principle of protection-in-intensity is that layered safety mechanisms growth safety of the machine as a whole. If an attack reasons one security mechanism to fail, different mechanisms may also still offer the important safety to shield the system.
Fail Securely
Handling mistakes securely is a key component of relaxed coding. There are two varieties of mistakes that deserve special interest. the primary is exceptions that occur within the processing of a safety manage itself. it is critical that these exceptions do not permit behavior that the countermeasure would usually no longer permit.
Don’t trust services
Services can refer to any external system. Many organizations make use of the processing capabilities of third-party partners, who probably have differing protection guidelines and postures than they do. it is not likely that you can impact or manage any external third-party, whether or not they're home users or primary providers or partners.
Separation of duties
It is a key concept of internal controls. It has two primary objectives. The first is the prevention of conflict of interest, fraud, abuse and errors. The second is the detection of control failures. Main goal is to ensure that individuals don't have conflicting responsibilities or are not responsible for reporting on themselves or their superior.
Avoid security by obscurity
It means it is a weak security control and in most cases always fails when it is the only control you can rely on. It is better to not to be reliant upon keeping details hidden.
Keep security simple
Attack surface vicinity and simplicity pass hand in hand. sure software engineering fads decide upon overly complex procedures to what would otherwise be exceptionally honest and easy code. builders have to avoid the usage of double negatives and complex architectures when a simpler method might be quicker and easier.
Fix security issues correctly
As soon as a security issue has been identified, it is the most important thing to address this issue and develop a test for it, try to understand the source of the issue. Usually, when we are talking about design patterns it is likely that the security issue amongst all code bases.
The security by design model appears differently in relation to less thorough methodologies including security through lack of definition, security through minority and security through out of date quality.
