Server operator faces many different types of attacks every day. Brute force, spam, CMS hacks and SQL injections are the most common - and the majority of them are automated botnet attacks. I think none of us can estimate how many servers and PCs are being unprotected against even the most simple botnets. But it’s not necessary to be a victim of an easily defendable attack.
But even being careful, one thing you can fail about server security is underestimating the risk of old vulnerabilities and botnets. Thinking they’re doing no harm anymore, since they have been exposed and tracked down.
Let us tell you, this is a big mistake believing that. Analyzing thousands of incidents every day, we are sure that hackers look at these tools as “oldie but goodie” ways to exploit Linux servers. In this article, we show you one good example, which became popular again lately.
ylmf -pc - Do you know this user agent?
We don’t think so. How many times had it appeared in your logs? Maybe a few.
And what should you do, if you see this name in your server logs constantly? All of us would ban this user agent or at least restrict its activity.
But frankly, it’s not a user. It’s the fingerprint of a widespread botnet.
Cutwail - A ten years old threat
In 2007, a botnet came to light. It was the Cutwail, which has been improved from a single HTTP request to a complex system (0bulk Psyche Evolution) through the years. Cutwail was responsible for 46.5% of spams in 2009.
Fun fact: according to Symantec’s research, 89% of emails in 2009 were spams. It was available for purveyors of botnets because of the geographical variation in the infected devices and better management of infected machines.
This botnet uses a really simple model. It infects machines with Windows operation systems with a trojan virus called Pushdo. Then the infected machine receives the instructions and the email to forward. Commands and emails come directly from a C&C server – in the early stages these were constant, but recently the C&C servers can periodically change as well.
When the bot is done with the task, sends a report to the C&C server with the statistics, just like when you use an advanced emailing service, but it's especially harmful and illegal. Of course, the whole communication is encrypted but it can be cracked if you’re tireless enough.
Security experts - after a huge attack against Twitter, PayPal, and CIA - have successfully stamped out the head of the network by cutting the connection from 30+ C&C and developer servers of this botnet.
During the investigation of this network, they found 120,000+ unique IPs online on a daily basis. Massive, isn’t it?
Weaker, smaller but still working
The head of the botnet has been cut, however there are some smaller networks on the Internet, so we can see recent activities as well. BitNinja found many infected devices these last months, thanks to the evolved techniques and unasked gifts of cracked software.
Here’s how the malicious scanning attempts we capture hundreds of daily look like:
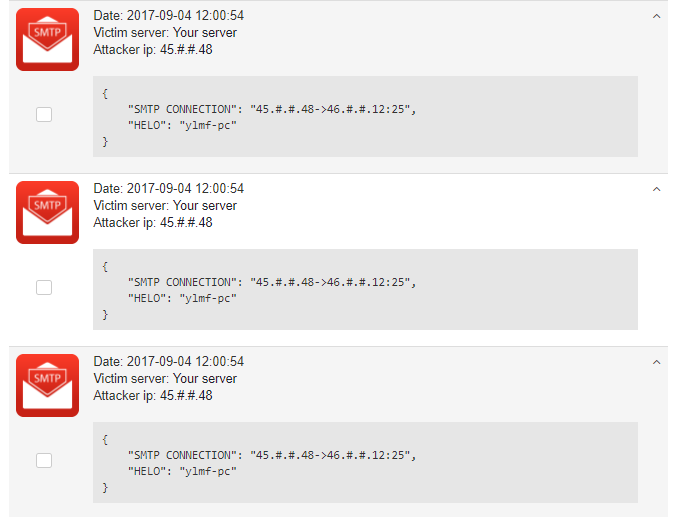
Protect your devices from Cutwail
Easiest solutions are the best. By following this motto, to remove the trojan virus, you only have to run a full virus scan on your PC. If you prefer any other solutions you can find some other ways how you can rid out of the Cutwail spambot.
Being a server operator, you can easily keep Cutwail spams away from your server with some additional IPtables rules
iptables -A INPUT -p tcp --dport 25 -m string --string ylmf-pc --algo bm -j DROP
or you can create an additional rule in BitNinja’s Log Analyzer module.
Stay safe!
