We’d like to start this year with a great announcement. Our purpose is to help make your servers safe and your service reliable. Your customers’ satisfaction is as much important for us as it is for you. That’s why we created a brand-new feature in order to make BitNinja more convenient for your users. This new module is called FTP CAPTCHA and it allows your visitors to remove their greylisted IP addresses when an FTP connection is opened.
What is the reason behind creating the FTP CAPTCHA?
If a greylisted IP wanted to connect to a BitNinja-protected server, the visitor could validate herself/himself only on HTTP and SMTP protocols. We want to give more opportunity for the visitors to remove their IP addresses from the greylist, so from the 1.25.0 agent version, the FTP CAPTCHA allows to delist greylisted IP addresses via FTP connections too.
How does it work?
When a greylisted IP connects to a BitNinja protected server on FTP protocol, thanks to this module, a fake FTP server will respond that there is only 1 file on that server.
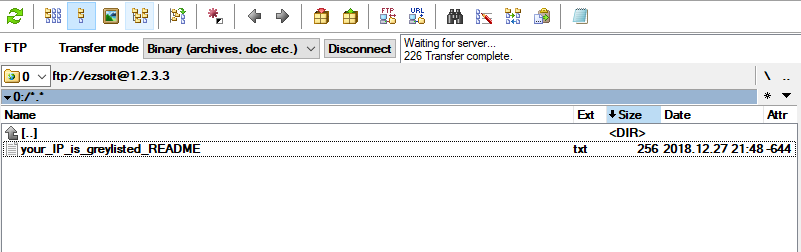
This file is the your_IP_is_greylisted_README.txt which contains the following:
Your IP has been greylisted by BitNinja.
To delist your IP, please visit the server using a web browser
and resolve the CAPTCHA if requested.
Please visit this URL: http://[server_ip]/
After you delisted your IP, you can access the real FTP server again!
Here is an example:
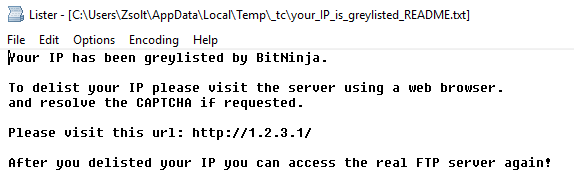
By following the instructions, the visitor is able to access the well-known BIC/HTTP CAPTCHA, where the IP can be removed from the greylist.
If the user ignores the instructions and doesn’t solve the CAPTCHA, then the IP remains greylisted. Those files which are uploaded from a greylisted IP via FTP (and not bigger than 1MB), will be placed into quarantine. You can find these quarantined files here: /var/lib/bitninja/CaptchaFtp/YYYY/MM/DD. The YYYY-MM-DD refers to the date of the file upload.
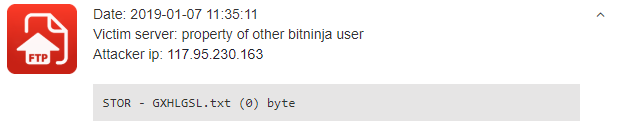
What’s more, this file upload will generate an incident on your server. This new type of incident will appear on your Dashboard like this:
If you are using a different firewall besides BitNinja, there are some pre-requirements which need to be
met if you want to make FTP CAPTCHA work on your server.
For more technical details, please visit our documentation site.
How can you enable it?
During the past few days, this module captured 380 incidents in our servers and we didn't perceive any major issue, so now, we give you the chance to be the first one who can try out the FTP CAPTCHA. While it is alpha, you can enable it in CLI:
bitninjacli --module=CaptchaFtp --enabled
After the successful test period (approximately 1 week), this module will be enabled by default. Don't worry, we'll keep you updated on this matter via newsletter. 😉
We are eager to get your feedback about your experience or help you if you need assistance, so don't hesitate to contact us at info@bitninja.io.
Upcoming features
We are planning a lot of new fancy features for this year. We’ve already given you a little hint in our year review article but now it’s your time to tell us what developments would you like the most. You can find many badass ideas on our Wantoo page. Feel free to add new ones or vote for each others’ wishes.
Of course, you can contact us anytime at info@bitninja.io or simply leave a comment under this article.
Stay safe, dear ninja!



