Our Attack Vector Miner (based on AI) is a very effective tool to identify 0. day attacks.
Here comes the first catch!
Discovery of a New Botnet
At the beginning of July, our Attack Vector Miner created a new cluster, filled with logs about a new type of botnet. We perceived the first incident on 16th June from an Indian IP address (106.51.152.115).
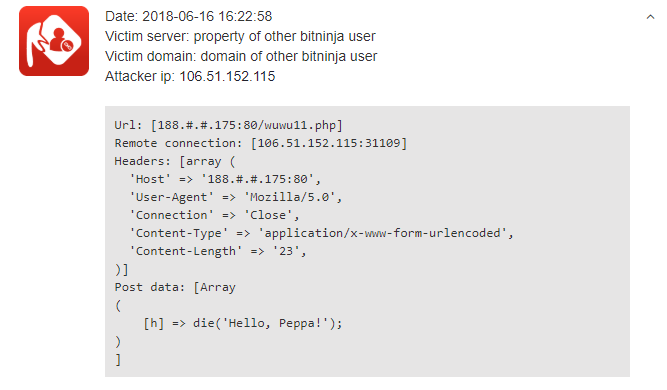
The first incident of the "Hello Peppa!" botnet
Since then, we have detected more than 120.000 attacks of this
botnet!
The Behaviour of the “Hello, Peppa!” Botnet
The specialty of this botnet is that the die ("Hello, Peppa!”) appears in the Post data
, as can be seen in the above screenshot. All attacks target the 80 port (HTTP) and use the Mozilla/5.0 user agent.
This botnet is like a hyena, which looks for the remaining meat left by a lion who has done the hard work. It searches for backdoors that were installed during a previous attack/infection by someone else.
Analyzing the Logs
As previously mentioned, we’ve detected more than 120.000 Hello Peppa attacks
between June 16th and July 20th. Following July 13th, the number of attacks began to decrease, but the flaw isn’t over yet.
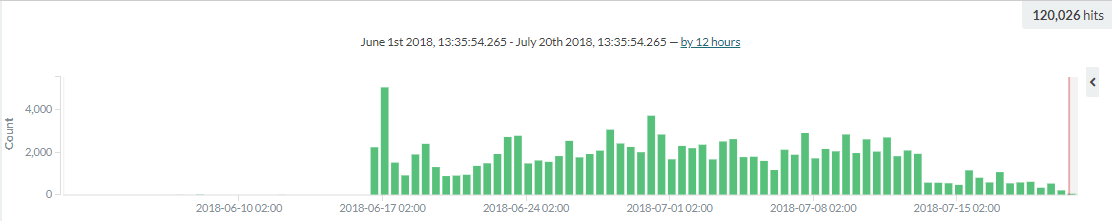
Number of "Hello Peppa!" attacks per day
Let’s see where these attacks are coming from.
| Top 5 Attacking Countries | % of “Hello, Peppa!” Attacks |
| China | 65.46% |
| Hong Kong | 9.68% |
| United States | 6.65% |
| Indonesia | 3.13% |
| Thailand | 2.64% |
| Total | 87.56% |
The top 5
attacking countries are responsible for more than 87% of the all "Hello Peppa!"
attacks. You can see from the table, that China leads this list by a significant margin.
From the next chart, you’ll see the distribution of the top 10 attacking countries:
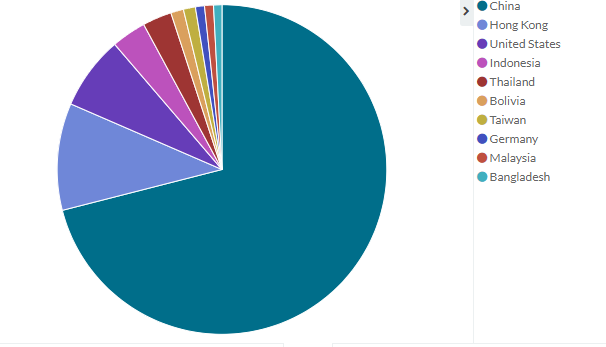
Top 10 attacking countries of "Hello Peppa!" botnet
Throughout the duration of our analysis (June 16th through July 20th), we experienced attacks from 1,141 IPs. The most frequently attacking IP has been 42.51.171.116 (China).
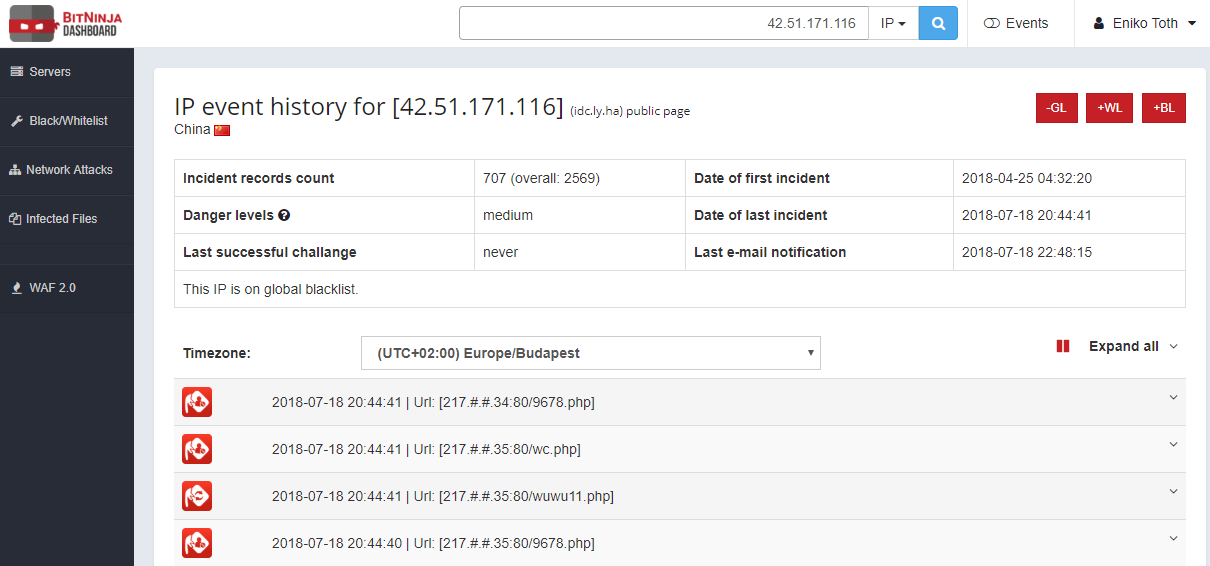
The most frequently attacking IP’s page in the BitNinja Dashboard
The following URLs were mostly targeted:
| /7788.php |
| /8899.php |
| /9678.php |
| /conflg.php |
| /db.init.php |
| /db__.init.php |
| /db_session.init.php |
| /mx.php |
| /qq.php |
| /s.php |
| /sheep.php |
| /w.php |
| /wc.php |
| /wshell.php |
| /wuwu11.php |
| /xshell.php |
| /xw.php |
| /xx.php |
The Protection Against the “Hello, Peppa!” Botnet is Here!
With BitNinja, you don’t have to worry about being attacked. In order to protect your servers, the only thing you have to do is enable the 404001 and 404002 WAF rules on the Dashboard.
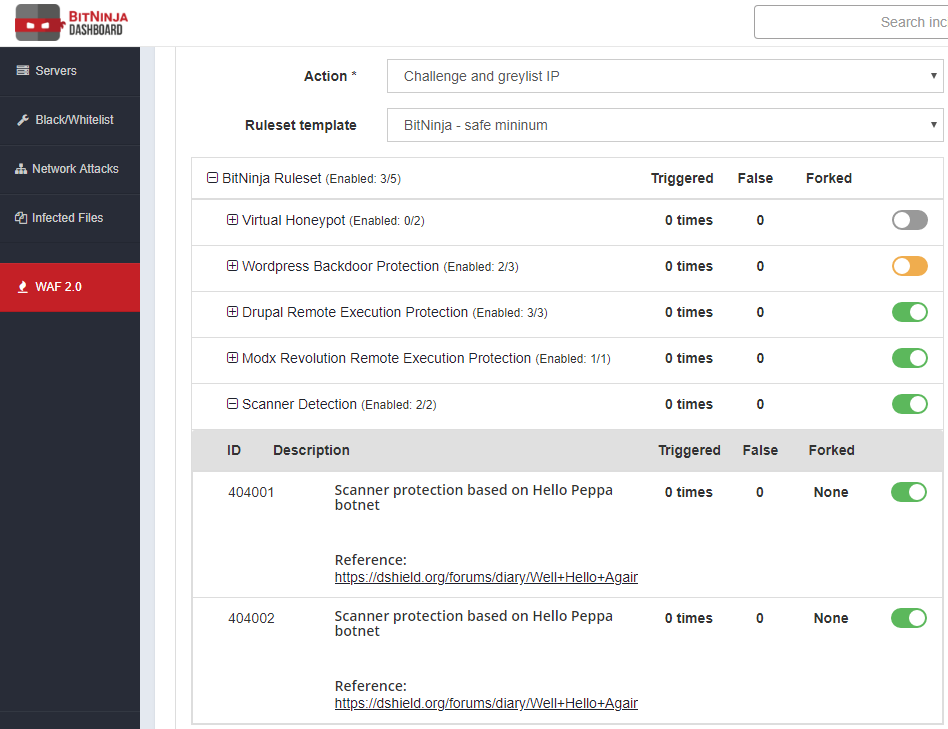
Here are some examples for the very first catches of these rules.
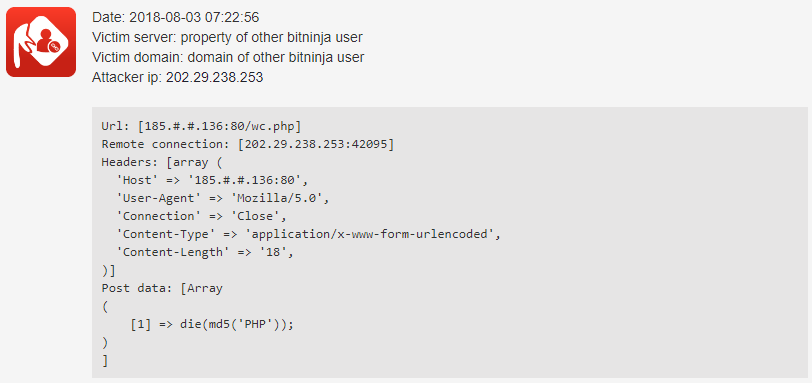
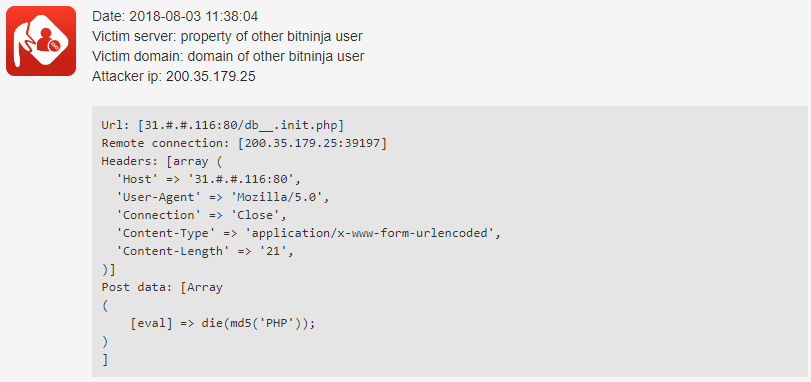
Since the rules' release, they have been triggered approximately 1052 times in the first 24 hours and 60 IPs were greylisted thanks to them!
Need help with it? Have a question? Leave a comment under this article.
Curious about the next catch of our Attack Vector Miner? Stay tuned! Soon, we’ll publish more. 😉







