Your server’s safety is the number one priority for us, that’s why we have created two new BitNinja WAF rules which are already part of the safe minimum ruleset. They grant protection against the following vulnerabilities:
Magento Remote Execution Protection
Those who are using Magento and didn't apply the patch are vulnerable to RCE (remote code execution) attacks. By targeting the “Cms_Wysiwyg” controller, the attacker can take over the site and gain information such as customers’ credit card details.
BitNinja will block requests sent to this controller which contain exact parameters like ’forwarded’.
WordPress Duplicator <= 1.2.40 – Arbitrary Code Execution
People use the Duplicator plugin for WordPress site migration and backup. According to the plugin’s official site, it has been downloaded more than 1 million times.
The Duplicator creates a compacted copy of the WordPress installation so that people can easily migrate their sites. Version 1.2.40 or older didn’t remove sensitive data after the migration, for example, the installer.php or the installer-backup.php. Using these files, the attacker could start remote code injection attacks through the wp-config.php.
If the attacker wants to send an HTTP request to these URIs (installer.php, installer-backup.php) our WAF detects it as an attack if certain exact parameters appear in the POST request parameters.
Be Protected by BitNinja!
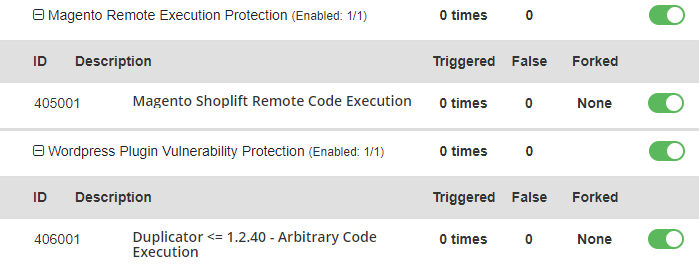
The following WAF rules provide protection against these vulnerabilities:
- 405001 Magento Remote Execution Protection
- 406001 WordPress Duplicator <= 1.2.40 – Arbitrary Code Execution
Here is an example log which was detected by one of these new rules:
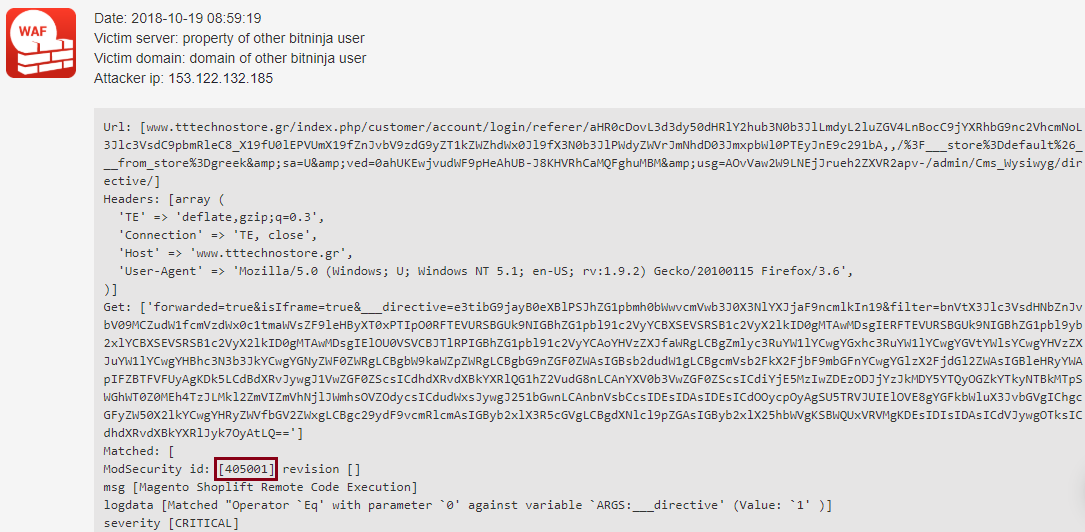
These rules are already enabled on your servers if you are using the WAF and you haven’t disabled them manually.
Make sure that the WAF 2.0 module is active on your servers in order to be protected against this kind of attack.
Aren't you using BitNinja yet? Don’t let hackers compromise your servers! Start kicking the hackers’ butts right now! During the seven-day free trial, you’ll see how many attacks are targeting your servers; after that, you will never want to leave your servers unprotected.

