RCE attacks
are one of the most dangerous types of attacks as hackers could take complete control of the victim’s host, meaning that they can run commands, install malware, etc.
In this article, I’d like to introduce 2 new vulnerabilities, which have been patched by BitNinja WAF:
- vBulletin RCE
- Rusty Joomla RCE
New botnet utilizes the vBulletin RCE vulnerability
In September, a new zero-day vulnerability was found in vBulletin
.
Nowadays, vBulletin is the most popular internet forum software, so this threat could affect many people.
The vulnerability (CVE-2019-16759) affects the vBulletin version 5.0.0 – 5.5.4 and allows hackers to exploit remote code execution.
With CVE-2019-16759, unauthenticated users can send specially crafted HTTP requests via the widgetConfig[code] parameter in an ajax/render/widget_php route string request.
This RCE vulnerability can be found in the includes/vb5/frontend/controller/bbcode.php and you can see the evalCode ($code) function in it:
function evalCode($code)
{
ob_start();
// find in: public_html/includes/vb5/frontend/controller/bbcode.php
eval($code);
$output = ob_get_contents();
ob_end_clean();
return $output;
}This vBulletin exploit has been disclosed and officially patched
, however, there is a new botnet that uses this vulnerability
to block other attackers from exploiting the CVE-2019-16759 on the victim’s server. This way, the botnet can own the server and other hackers won’t be able to utilize the same server.
How can the botnet own the victim’s servers?
The botnet modifies the vulnerable source code, so it requires a password for anyone to run a command with it.
function evalCode($code)
{
ob_start();
if (isset($_REQUEST["epass"]) && $_REQUEST["epass"] == "xxx") { eval($code); }
$output = ob_get_contents();
ob_end_clean();
return $output;
}
Rusty Joomla RCE – exploitation of PHP Object Injection
CVE-2015-8562 is not a new vulnerability, it was discovered in the wild and patched in Joomla 3.4.5. However, an Italian researcher found a PHP Object Injection which is quite similar to CVE-2015-8562
The differences are:
- The new RCE (which doesn’t have a CVE identifier yet) is completely independent of the server environment (while the 2015 vulnerability can be exploited only on PHP versions before 5.4.45, 5.5.29 or 5.6.13)
- It only affects the Joomla 3.x (while CVE-2015-8562 affected all Joomla versions)
Here you can see the zero-day in action:
You can find the researcher’s full technical explanation here
.
Protect your servers with BitNinja WAF 2.0
The good news is that BitNinja users were protected from the very first moments of these RCE vulnerabilities. The 933130 and 933150 WAF rules are keeping BitNinja-protected servers safe against the above-mentioned threats.
These rules are in the OWASP Core Ruleset -> PHP General Attacks -> 933130 - PHP Variables & 933150 - PHP Functions: High-Risk PHP Function Names

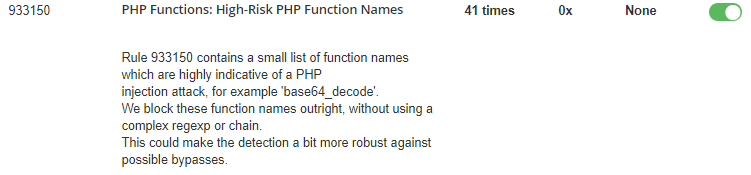 They are both parts of the BitNinja Recommended ruleset, so if you are already using that ruleset, you don’t need to do any manual intervention.
They are both parts of the BitNinja Recommended ruleset, so if you are already using that ruleset, you don’t need to do any manual intervention.
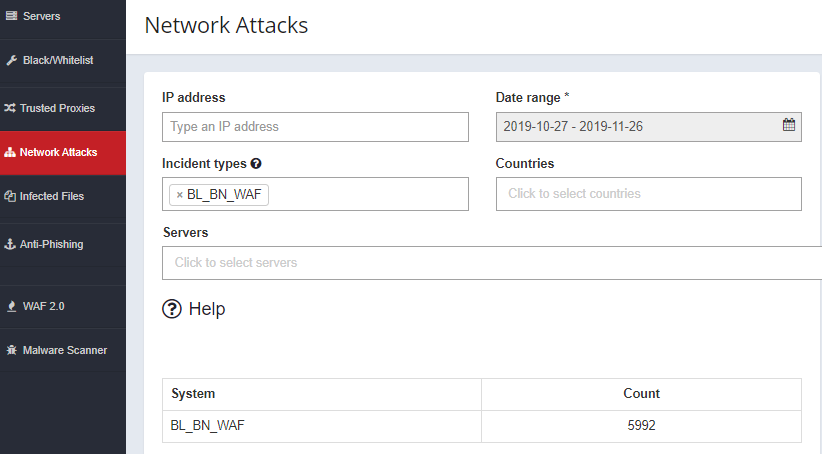
When these rules are active on your server, the hackers won’t be able to exploit the mentioned vulnerabilities. In the Network Attacks menu, you can find these logs easily at any time. Simply choose the BL_BN_WAF incident type and you’ll see the requests which were blocked by the BitNinja WAF.
If you are not part of our Ninja Community yet, join now and keep your servers safe against vBulletin and Joomla RCEs – and, of course, against many other types of attacks 😉
Try out BitNinja with the 7-day free trial
 They are both parts of the BitNinja Recommended ruleset, so if you are already using that ruleset, you don’t need to do any manual intervention.
They are both parts of the BitNinja Recommended ruleset, so if you are already using that ruleset, you don’t need to do any manual intervention.