The onset of the Internet has brought many rewarding benefits to human race. Thanks to it, communication that was pegged to letters, faxes and phone calls back then, have now become faster, reaching more audiences. Social media has also made it possible to connect with people from all around the globe. Although, with this new communicational development comes the challenge of phising and spamming that has continued to disrupt the new mailboxes of thousands of people around the world.
Spamming and phising can both be a form of stealing, by a hacker, where a great number of people are targeted worldwide. It can take several forms. For example, an email message can be sent to you in the guise of a person you know and trust. This method is quite effective, though cybercriminals found a much better way of getting your attention and treasured personal data, through the use if malware.
Malware takes on many forms and all of them have a common goal; to infect a targeted person’s computer and obtain whatever the malware was sent out to. Common forms of malware include spam mails, ransomware, adware and computer viruses. The most common form is spamming, which is used to attack millions of unsuspecting victims, via sending unsolicited emails.
You have perhaps heard of spam campaigns and wondered what they were all about. They are highly effective in spreading malware due to their high volume. They can collect data on active email addresses as well as keep a list of it for the hacker for future usage. Most of the people targeted are from affluent nations such as the US, Germany, Russia and China. These countries are the ones where most people make good use of technology and have most of their sensitive information stored in websites they visit to play computer games, make purchases with credit cards and even transact banking while online. This has provided attackers with the breeding ground from where they can conduct massive spam campaigns that are proving to be very effective. Spam campaigns work in an easy way:
1. Attacker locates multiple botnets
The attacker locates botnets mainly from the aforementioned countries from where they can conduct the attack. Botnets are computers that are already infected by a virus that helps sending spam messages to targeted victims. The owners, whose computers are being used as botnets, are often unaware of this and the attackers use these computers to deliver and at the same time receive messages from the targeted computers. Thus, sending spam messages becomes easy and cheap, as the computer owner’s resources are used instead of the attackers’ resources.
2. Attacker prepares email for victims
Spam can take the form of viruses which collect sensitive information belonging to the computer owners. Hence, if the computer owners used only online services to make purchases or to save some data, these will be forwarded to the attacker. This helps the attacker in the understanding of the target person as well as of the organizations they communicate with. the message the attacker creates will be thus sent directly to the targeted person’s inbox and be addressed specifically to them.
3. Unsuspecting victim opens the email
Here is where the actual actin begins. Those who do not take the advice of not opening emails from someone you do not know often fall victim and click on these emails. Even more appalling is the fact that the attacker might use spam message that includes the name and sometimes even the logo of a certain institution that the victim communicates with and fully trusts, such as bank or the tax department. The individual may thus be less inclined to think that it is a spam attack, and proceed to read the email. These mails may often have link or attachments which may direct the victim to take further action, and upon clicking on them, the malware begins to download on their computer. This may be ransomware, like CryptoLocker, that encrypts very important files and asks for money to be paid in order to obtain the decryption key from the victim, or even other financial malwares that steal username, passwords, credit card details and bank credentials of the victim. The machine can also be used as a botnet, further increasing the number of computers used as botnets in sending spam emails.
4. Expansion of the botnet
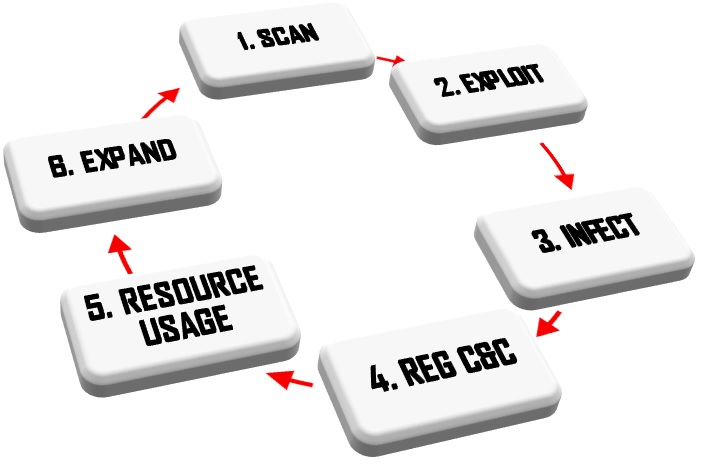
The aim of botnets is not only to exploit the vulnerabilities of targets but to make them to download the infected code, so they become infected too, and line up as a new member in the zombie army of the botmaster. In most of the cases it is enough for the innocent user to click on the malicious link, since after this the attacker will get access to the file. If you are interested in the detailed explanation of a botnet’s lifecycle, see out previous blog entry about it, and about the possible defense methods here.
What makes them successful?
Spam campaigns have been successful largely due to the lack of education on the cyber security threats what most computer users should invest in. Thus, the attackers rely on human curiosity as well as trust in organizations that the victims are in contact or do business with. Curiosity will make you want to click on a link and see what is being offered, and trust in an organization will make you want to download a newsletter that has been sent to you.
Forms:
It might be of help to know the kind of spam campaigns that are still in use in trapping millions of people. One, is the Nigerian scam, where the victim is promised a large amount of money, which will be delivered only when they pay a small fee upfront. If the victim pays the requested fee, further excuses are made in order to obtain more fees and then the bad guy vanishes after collecting what he deems to be enough.
Another type is malvertising, which is a kind of advertisement that contains a malware and upon clicking on it the infection starts to spread. They usually promote products which offer miraculous recovery from illness and ailments, such as pills that help reduce weight in days or pills that instantly enhance sexual drive. These are often geared to the curious minds who unsuspectingly purchase the said product online, only to realize later that the product does not even exist. For example, read our previous article on malwares and recent malicious incidents.
There’s also the greeting card spam message that is sent purportedly by your “friend” living abroad. You will have to click on a link to download the greeting card, which often leads you to download the malware at the same time. Another, is the travel spam, where you are offered such great deals and discounts for travelling, which are often too good to be true. There are also the spam emails that invite you to invest in a certain real estate that turns out to be non-existent.
Moreover, other subtle spam mails turn out to be malwares including online dating messages sent to you from potential candidates from your “area”, emails from your bank informing you of a potential breach to your bank account and then asking you to change your password through a provided link that will likely to ask for username, old and new passwords to your bank account. Furthermore, there is the post office spam that alerts you to a missed mail which you can access by clicking in a link for details. Even more alluring is the “get rich quickly” scam, where you receive an email stating that there are ways in which you can double, or even triple your income. A huge number of people, especially the young fall prey to it.
The above mentioned examples of spam mails are not at all exhaustive, but share certain characteristics in common. They ask for your username and password to sensitive accounts containing your personal information or financial details or ask you to click on a link that redirects you to some fishy website. Others, however, can be more direct and specifically ask you for certain favors, failure to which will lead to certain consequences.
The business of malware and cybercrime continue to bloom due to social engineering or the human touch that the attackers are very good at manipulating. Educating oneself and the organization in the forms of malware as well as spa emails is greatly encouraged for everyone, to be safe from such attacks. Deleting spam emails without the thought of treading them is highly recommended. Users should also be educated on the importance of installing anti-virus software.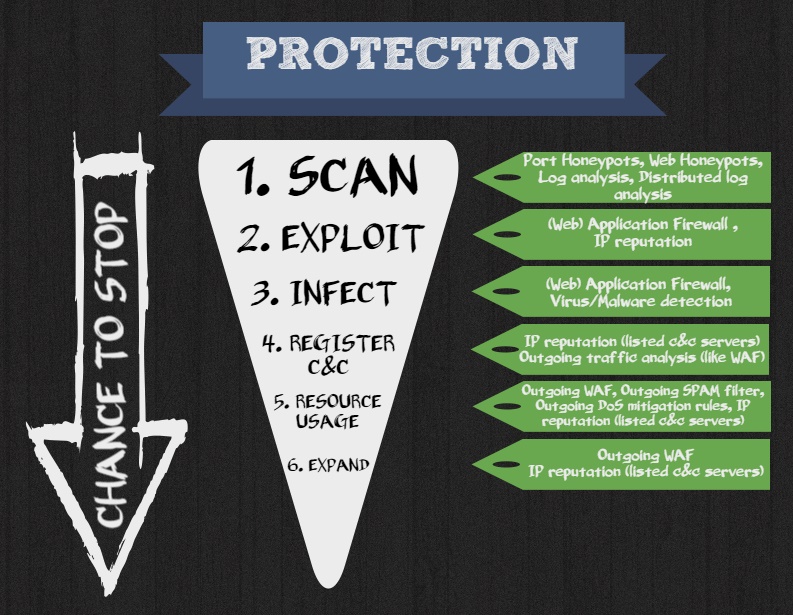
Will spam campaigns end in the real future? Very unlikely. Since the Internet still has numerous loopholes that are yet to be properly sealed. Until that time when we can say that the Internet is completely safe from cybercrime, no one should let their guard down when faced with unsolicited emails attachments. Despite the unpredictable situation, there are several server security softwares, like Bitninja, which are designed to block these attacks at every stage of the activity, starting from the scanning fight until the final stage of expansion.


