Since the first emergence of computer viruses and botnets, the number of infected machines is growing day by day. The rapid development of IT not only brought increased comfort to our life, but the vulnerability of our personal data as well. In parallel with the evolution of technical devices, hackers became more sensible, aggressive and pragmatic each day. How does this phenomenon affect today’s world?

The real threat
Well, nowadays the number of infected and compromised servers can be estimated to 45 million. Yes, this number is quite shocking, because the everyday Internet user would think that they are safe from all kinds of attacks. Although, statistics just reveal the opposite. Did you know that every newly configured server falls prey to hackers’ attempt in 2 days? According to the estimates of the security industry, the attacks directed against particular servers caused more than $110 billion loss to server owners and companies worldwide.
Know your enemy
Before you would dash to your computer and would insanely start looking for evidences of malicious activity, it is imperative to know your enemy. Or else, how would you be able to fight against them? To discuss this issue further, we need to mention some harsh facts, that may affect the server owners sensitively, but we still need to talk about them.
- An average server receives more than 1000 different kinds of attacks each day.
Tough, isn’t it? Your server may not be an exception either.
- 92% of the different scans are malicious.
Though, there are some harmless net crawlers, who just serve as an innocent information-gathering device, e.g. Google crawler, but admit it, today’s tracking instruments ain’t all serve the innocuous users’ benefit.
- 1/3 of CMSs (Content Management System) are vulnerable.
75% of CMSs, platforms like WordPress, Joomla or Drupal, are based on an open-source code, and are used by large number of users. These are popular targets of cybercriminals, as every source is available for them to break into individual servers.
- The majority of attacks work in auto-pilot mode.
Most of the attacks are automated and not targeted. According to the research conducted by Radware Security, automated bot attacks will lead the cyberattack innovation in 2016. The results of their research look as follows: “90% of 300 companies surveyed experienced a cyberattack, and half of those attacked experienced short, intensive attacks-up from 27% in 2014.”
What is the point?
Well, OK, they infect my servers with their viruses and stuff, but why is it advantageous for them? Actually, it can have several reasons, but they obviously do it in the hope of some personal profit, let it be getting hold of your credit card credentials or accessing illegitimate websites from your computer.

The most popular cyber drives are:
A perfect example for this is the well-known Anonymus upheaval. Never heard about Anonymus? Check this out!
This should not be new to anyone. Hackers are undeniably working to steal our personal data, log in details for our PayPal etc., so they can use our credentials for their own online purchases, hiding their own footsteps in the cyberspace.
Have you heard about the “Deep Web” before? This is the bottom of the iceberg, that average Internet users won’t reach with basic search engines like Google, Yahoo, Bing etc. It contains 500x more websites than the “normal web” and has a size of 7,9 Zettabyte. The “Deep Web” has a segment that is called “Dark Web”, which was originally created for governmental purposes in 1990, but in 2004 they made it available for public use. The average user only needs Tor (which provides you full anonymity and access to websites on the “Dark Web”) to be able to access this deeper strata of the Internet. What kind of people are using it, and what can one find there? Well, it is mainly used by drug dealers, hackers, pedophiles and other criminals who are seeking for useful information that makes their “business” easier.
How can hackers make profit from using this option? There are some mischievous companies, whose objective is to take down their competitors’ websites or services, so they can get ahead of them in the competition for the best places in that specific market segment. They access the “Dark Web” and contact a professional hacker, than they pay a nice amount of money for him/her to send a DoS/DDoS (Denial of Service) attack on the opponents’ webpages, so it will be unavailable for their customers and clients. Or just to hide black hat SEO scripts into website codes. Easy, isn’t it?
The aim of this is to steal or erase sensitive data from an established organization, so their power can be questioned, or weakened.
The bigger a hacker’s zombie-bot-army is, the more powerful it gets. They are looking for new fellow-soldiers by scanning the weaknesses of each server and by taking advantage of its vulnerabilities, so finally they can enslave the server as a new member of their botnet.
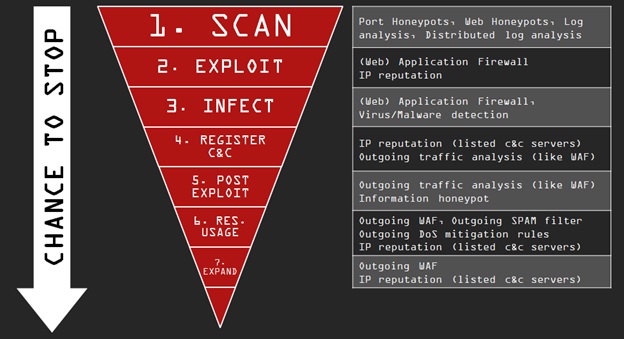
Attack Cycle
The deeper the hacker gets into your system the harder you can fight against them. That is why it is extremely important to round them up as early as we can. You can read more details about the attack cycle and how to protect your server against the bad guys in each step of the assault in our previous blog entry.
5 Attack Trends to Watch in 2016
- The return of largely spread threats like CryptoLocker and Dridex
CryptoLocker is a kind of a trojan virus, that first emerged in 2013 and it was spread through innocent looking emails sent by a company that actually seemed legitimate. The email contained an attachment, if someone opened it, it installed itself immediately, and encrypted the files on the compromised computer demanding a ransom to provide the decryption key needed to decrypt the files. It is thought that the designers of CryptoLocker has compelled almost $3 million from the innocent victims of the virus.
Dridex is a malware that infects Microsoft Office, leveraging macros. When the computer has been compromised hackers become able to access banking credentials and personal information of the user.
- The rise of destructive cyberattacks
With the growing number of hackers and malwares and with the evolution of IT, the number of possible victims of cybercrime is still increasing. However, there has been a recent shift in the trend of attacks, because previously they were targeted against private individuals, but nowadays they are pointed towards governmental sites, power plants, financial institutions, and vulnerable sites of respectable companies. The bad guys are changing their techniques all the time, and it gives a throbbing headache for the security industry.
- The arrival of “knowledgeable” hackers , who learn targeted systems
As I have mentioned before, botnets are the ruling power of cyberattacks today, and they all need a king, who can control and manage them easily, someone who has powerful and up-to-date knowledge about the most recent issues in the Information Technology. These are the upcoming generations of practiced hackers, even masters of social engineering, with whom we need to face soon enough, and those, we are facing already.
- Wearable Tech risks
Wearable technology is more widespread now than ever before. Unfortunately, it has its own risk factors, too. For instance, your privacy may be invaded, facial recognition in digital glasses can identify any stranger, and some medical devices have proven to be hackable.
- New open source vulnerabilities and the use of known ones
WordPress, Joomla and Drupal, and other open-source based solutions are widely used by server owners and administrators, this is what makes it a sore spot. The hackers have every source to break into their system and perform any unsolicited activity on it. We live the age of zero-day attacks now.
4 factors for strategy change
- High risk, but still low support from the base
- Huge competence shortage, no dedicated stuff for security problems
- Sometimes significant increase in budget
- Too many targets to aim at, and no clear strategy
BitNinja is an easy-to-use server security tool which protects your servers/websites against 99% of cyberattacks.


