No matter if you’re a Linux security veteran or you’re just about to get your feet wet, you’ll face the same security threats and upcoming attacks forms. Here we come with a security cheat sheet with ultimate checkpoints that no sysadmins should miss.

When meeting new company, usually the very first thing I’m asked about is „How should I get rid of hackers? Show me the silver bullet.”
But it’s a little bit like asking an economist on „Where to invest my money?”. It depends.
To get a grip in the jungle of security recommendations, here I collected some guidelines from our executive team to come in handy – no matter your company size, industry or level of expertise.
1.Don’t underestimate the impacts of poor security
There is a tendency to think that a software will cover up all the security holes at once. However, security is not really an application, it’s rather an approach. As hacking attempts can reach your company in many ways, there’s a lot of frontiers to take care about from secure coding, through web application security, to password management.
And that’s why poor security is worse than no security at all.
It leaves you with the false feeling of security and has an effect on many aspects of your business and yourself:
- your support load
- your expenses
- your team’s stress level
- your development costs
- your business reputation
If I asked you, could you tell how much money is spent on security at your company – considering all these side-effects?
Server security is simply too important and poses too many threats to neglect it.
2.Hire hackers to pentest
Let me just start with there’s no unbreachable system and never will be. So despite the fact that the word ’hacker’ means something evil for the majority of the world, penetration testing (intrusion detection or red teaming) is not a wicked thing to do.
Hackers will bring extraordinary experience to the table when it comes to challenging your shields. And the result is transparency in current weaknesses and a great security strategy to move on with. Deal?
No matter if you hire a pentester company to do the job or use a crowdsourced platform, like HackerOne, the benefits are the same:
- It will open your eyes in terms of uncovering holes/blind spots/attack vectors.
- It helps to prioritize your risks when you don’t know where to start.
- It helps to get better in safe development.
- It improves your team’s security response time for sure.
As your systems evolve, new attack factors will be born with every new extension and application on your servers. So, form a habit and pentest regularly.
3.Automate, automate, automate
Automated bot attacks have been dominating the security landscape for years now. And you know, „fight fire with fire”: security automation is the best tool against automated attacks and for your peace of mind.
Do more in less time.
Automate your processes, take control of your incident response and shorten the time between detection and response with automation. You may underestimate it can save you, but trust me, it does wonders.
4.Manage your whole infrastructure in one place
When we think about deploying and managing a security toolset of servers, there might be a conflict of interest in the air. Engineers, working in symbiosis with the servers through control panels, might prefer to handle security management this way also. But this is where you have to stay business-focused instead. Here’s the reason why.
Using security information and event management services (SIEM) provide a centralized view into an infrastructure. They support your processes, analysis, and reporting, offering great benefits:
- It enables you to react faster by cutting back the amount of information you have to go through in each case. You can identify issues a lot faster and lower the damage at once.
- Having all relevant security data in one place, it’s easier to recognize outstanding – hence suspicious and potentially harmful - trends or patterns.
Take a look at all the security information and security events from all over your network. Use SIEM.
5.All-in-one security suite vs. single-point solutions
With the popularity of nowadays’ single-point security solutions, it’s no wonder that engineers struggle with incident handling and orchestrating their software environment. As many solutions are not designed to work together, it’s a waste of time and money to handle things this way. Control your security costs, before they control you.
But of course, having only a firewall is not a good solution either. Just think about the airport vs. castle model approach we wrote about earlier.
We suggest to find a comprehensive, all-in-one security solution
with several security modules against different threats.
Make duplications disappear, exit the jungle of complicated server security and enter the world of effortless management.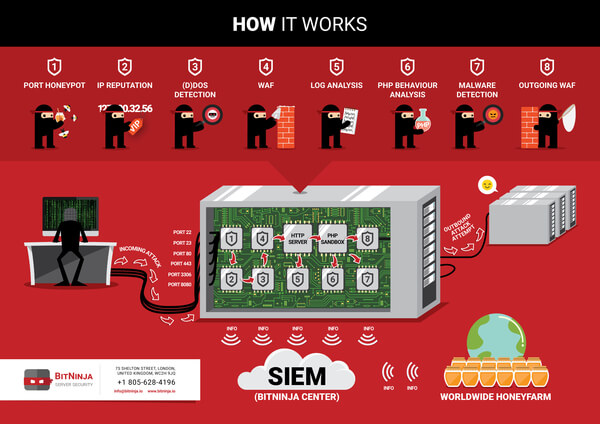
+1 Try BitNinja
If you’re fed up with struggling all the security issues mentioned above, try BitNinja. Put your attention back on your business and don’t let hackers distract you from your core focus.
Sign up for the free 7-day trial here.


