As 2019 will be over soon, it’s time to stop for a while and look back on what happened this year.
2019 was a unique year at BitNinja (you’ll see on the results). We got closer to our mission – making the internet a safer place.
However, we couldn’t have reached the successes mentioned below without our ninjastic partners. Many new features were inspired by the Ninja Community. Also, the continuous feedback that we are receiving from day to day about how BitNinja changed businesses’ life for the better is a huge motivation for us to keep working harder and harder every day.
So, we’d like to say a huge THANK YOU for everyone who follows us on our road. We hope that our ninja friends enjoyed this year as much as we do.
Let’s review 2019:
BitNinja Timeline of 2019
This year, we developed several industry-first features to provide the most advanced server security suite that hosting companies could have. This point, I’d like to highlight the importance of customer feedback. Most of these developments were requested by our partners and we truly care about these wishes, so we made those features available. So, we encourage everyone to share ideas with us on our Productboard Portal
.
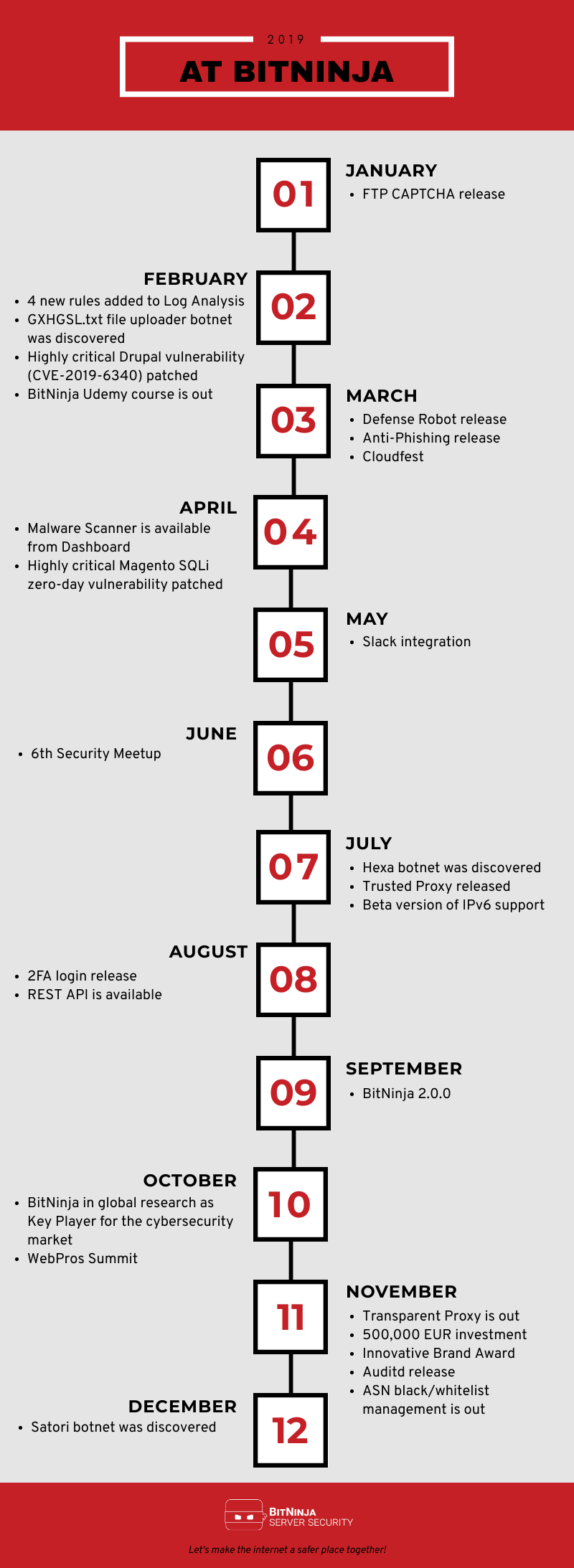
January
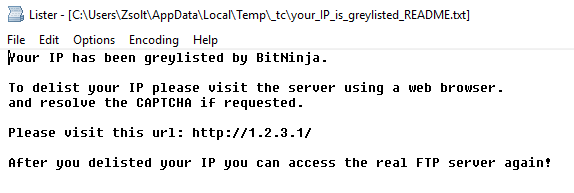
- NEW FEATURE - We started the year by improving our CAPTCHA modules. We released the FTP CAPTCHA , which not only allows delisting the greylisted IP with the CAPTCHA on FTP protocol too but also helps us to discover new kind of attacks (see it between the February’s events).
February
- NEW RULES - The BitNinja Log Analysis (=SenseLog) module was updated with 4 brand new rules and a 5th rule was also optimized. These rules stop Magento Downloader botnet, WP-login attempts from deprecated User Agents, Plesk login fails, suspicious IPs from LFD and XML-RPC attacks.
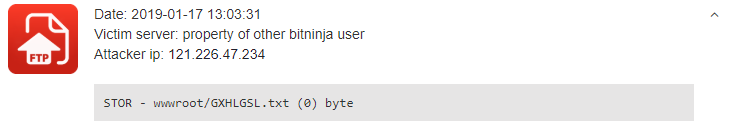
- BOTNET - The new FTP CAPTCHA module which was released in January helped us to discover the GXHGSL.txt file uploader botnet . The module not only helped us to catch this botnet but also provides protection against it.
March
- NEW FEATURE– The BitNinja Defense Robot is a breakthrough innovation
for the cybersecurity market. This is the first real-time & automatic malware root cause analysis, which finds the origin of the malware upload and the malicious IP will be automatically blocked. - NEW FEATURE – In order to help our customers to discover phishing content on their servers, we released the new Anti-Phishing feature.
- EVENT – We are regular exhibitors at Cloudfest, so we didn’t miss this year either. We met many interesting people, old and new customers as well. It was great to have inspirational talks with those guys.

April
May
- NEW FEATURE – We know, that receiving important security notifications immediately is a key factor to keep a server’s safety up-to-date. So, we created a Slack integration to enable immediate BitNinja alerts.
June

July
- BOTNET – The new Defense Robot module (released in March) helped us to discover a new kind of botnet. We named it as Hexa botnet, as it is using hex coding. The Hexa botnet is targeting WordPress hosts
, however, the newly added BitNinja WAF rules will keep them safe against this threat. 😉 - NEW FEATURE – The increasing number of attacks coming through Cloudflare and other proxies/CDNs urged us to develop the brand-new Trusted Proxy module, which traces the hackers’ real IP, so they can’t hide behind proxies anymore.
- NEW FEATURE – The beta version of IPv6 support is out.
August
September
October

November
December
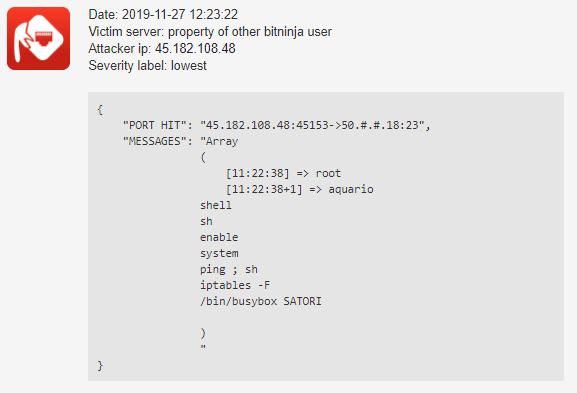
- BOTNET – New IoT botnet (Satori botnet) was discovered and stopped by BitNinja.
Cyberattack statistics of 2019
2019 was no different than any other year. Cybercriminals are still not resting and hackers are using more sophisticated techniques from day to day. It was a challenging year, as we had to face different kinds of cyberattacks and fight back against them to keep our ninja friends’ servers day and night. Let’s see how BitNinja performed in 2019:
Cyberattacks increased by 200%
In 2018, BitNinja stopped a little more than 1.5 billions of attacks. The total incident counts of 2019 (until 18 Dec) reached 2,882,188,192. As a half month of data (19 Dec - 31 Dec) is still missing from it, we assume that this number will grow around 3 billion, which means a 200% increase from 2018 to 2019.
In the chart below you can see how these attacks were distributed throughout the year by months:
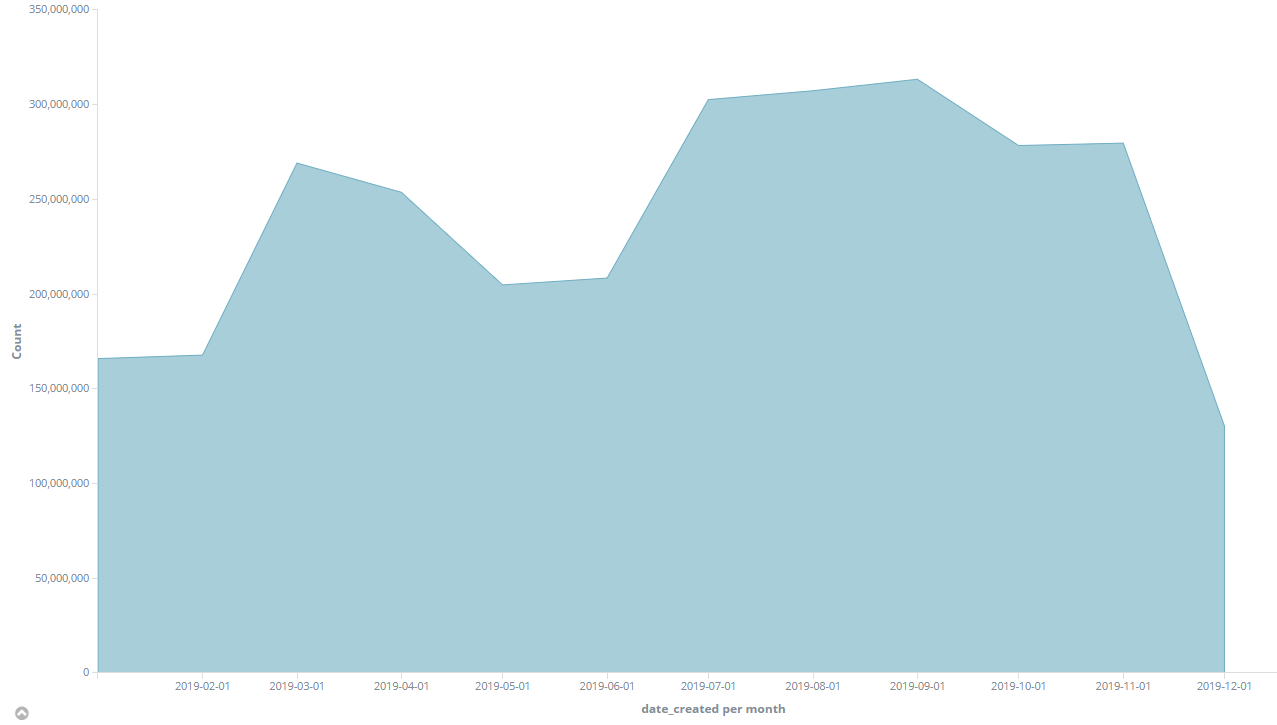
What does this huge number mean for each server? A BitNinja protected server was saved from averagely ~1500 attacks every day, which could cause serious damages without our protection.
Incredibly low false positive
We are very proud of our invention, the greylist, which helps us to reach an incredible low false positive rate. Comparing to last year, we could even decrease this low number even lower by 16%!
In 2019, our average false positive rate was 0.67%, which means that from 1000 blocked requests, only 6 were blocked falsely by BitNinja and these falsely blocked IPs could delist themselves with the convenient Browser Integrity Check
or Google reCAPTCHA.
Telnet scanning is still the hackers’ favorite
We always highlight the importance of prevention in the cybersecurity. We believe that it’s much better to avoid the problem instead of solving it after sh*t happened. Still, a lot of people don’t know (and unfortunately most of the security vendors still focusing only on the reactive solutions) that the first step of the infection cycle
is the scanning.
That’s why our customers love our Honeypot modules because they stop the bad guys at the very first stage of an attack.
The all-time-favorite port to scan is the 23 telnet port, so it’s not surprising that it leads our list:
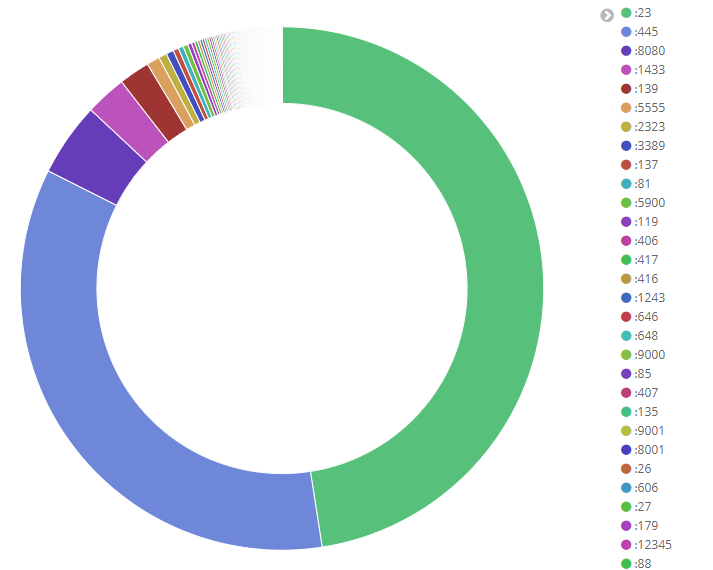
The 23 port was used to remotely access a server a long time ago. Nowadays, people don’t really use it, but even if the hackers find 1 open 23 port from 1000 scans, they could gain root access to the server and cause serious damages.
The second most scanned port is the 445 port, which has the same purpose as port 23, the only difference is that it works on Windows hosts.
Prevention is the key factor for success
As mentioned in the previous point, scanning servers for open ports and unpatched vulnerabilities is the first step for hackers. So why not to stop them at this stage, instead of letting them hack your servers?
We collected how many malicious requests were blocked by the different BitNinja modules and the Port Honeypot module is still on the top. However, comparing to 2018, we experienced even a higher range of blocked port scanning attempts. The Port and Web Honeypots are responsible for 85% of the total incidents caught by BitNinja this year.
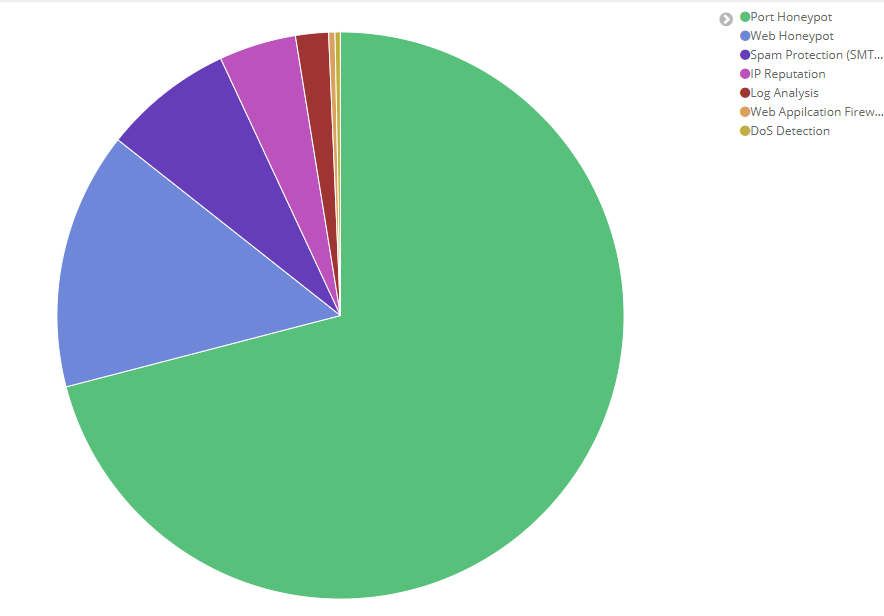
I think this pie chart presents perfectly how BitNinja protects the servers in a proactive way and we catch the bad guys before they could run any malicious code on it, have access to your data or use your servers’ resources.
WP-VCD malware on the rise
Malware infections can be daily struggles for those IT teams, who doesn’t have a powerful security system. This year, many new customers asked our help to clean their servers and provide an ultimate solution for their servers’ safety.
Detecting 2,816,734 malware in 2019 is a nice result, however, we’d like to highlight one type of malware from them.
This is the WP-VCD malware that affects WordPress sites. We added a new pattern to our Malware Detection module in July to secure our partners from WP-VCD.
Since these rules’ release, this is the leading malware in our database. Since July, we quarantined more than 200,000 files that were infected by WP-VCD.
Wordfence published a report
about this malware in November.
Web attacks are huge threats for hosting business
Shared hosting servers’ biggest attack surface is the hosted websites. Outdated CMS systems (WordPress, Joomla, Drupal, Magento, etc) make servers vulnerable for different kinds of cyberattacks, like SQL injection, cross-site scripting (XSS), remote and local file injections and many more.
The BitNinja WAF 2.0 is a powerful tool to keep websites and servers safe against these threats. Our WAF blocked more than 10 millions of cyberattacks in 2019.
Here you can see the Top 10 rules:
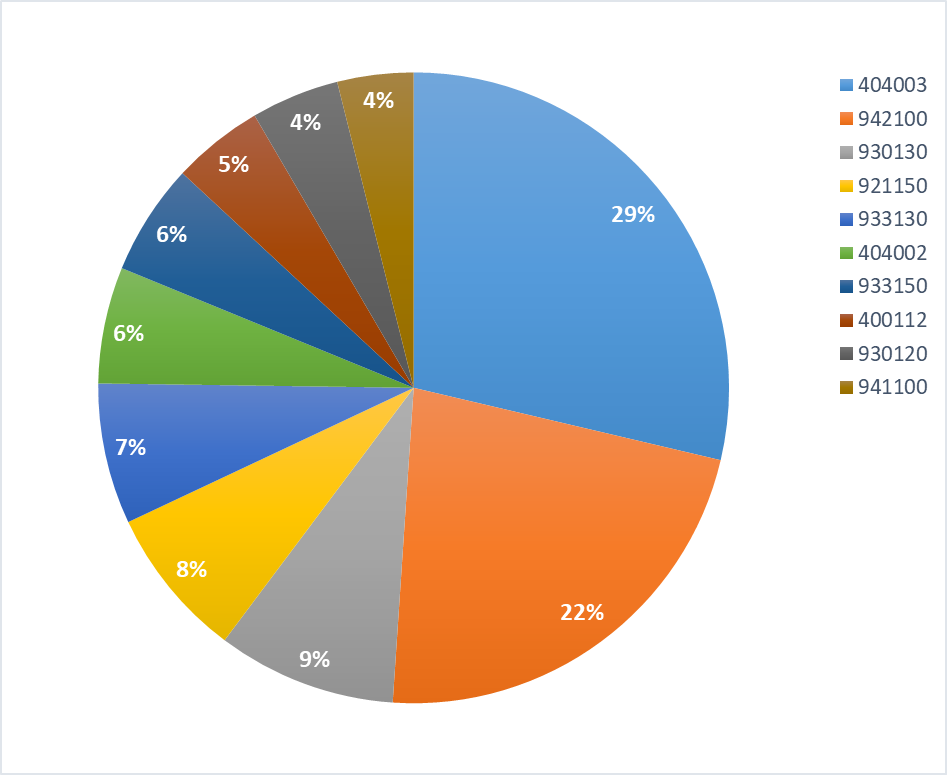
| Rank | WAF Rule ID | WAF Rule Name | Incidents |
| 1. | 404003 | Scripting user agent protection | 2,299,198 |
| 2. | 942100 | String Termination/Statement Ending Injection Testing | 1,793,333 |
| 3. | 930130 | Restricted File Access | 735,333 |
| 4. | 921150 | Checking for GET arguments | 622,876 |
| 5. | 933130 | PHP Variables | 578,464 |
| 6. | 404002 | Scanner protection based on Hello Peppa botnet | 478,828 |
| 7. | 933150 | PHP Functions: High-Risk PHP Function Names | 458,244 |
| 8. | 400112 | Virtual Honeypot | 374,575 |
| 9. | 930120 | OS File Access | 361,839 |
| 10. | 941100 | Libinjection - XSS Detection | 312,694 |
We are happy to see that 3 rules created by our tech ninjas (404003, 404002, 400112) are in the Top10 list. Our team is regularly updating the rulesets with new kinds of rules to patch zero-day vulnerabilities, stop newly discovered botnets and prevent serious web attacks.
Ensuring hosted sites’ safety should be a number 1 priority for hosting companies, so if you still don’t use an advanced Web Application Firewall, try out BitNinja for free with the 7-day free trial which can be used on all of your servers.
Sign up for a free trial
WordPress sites are the most vulnerable
More than half of the websites all around the world run with WordPress CMS, so it’s not so surprising that WordPress sites are the main target of hackers. Yet, many WP site owners don’t care about security.
We label a different kind of attacks with BNVL labels and here is the Top 15 list of the most popular attack types which were blocked on the BitNinja protected servers:
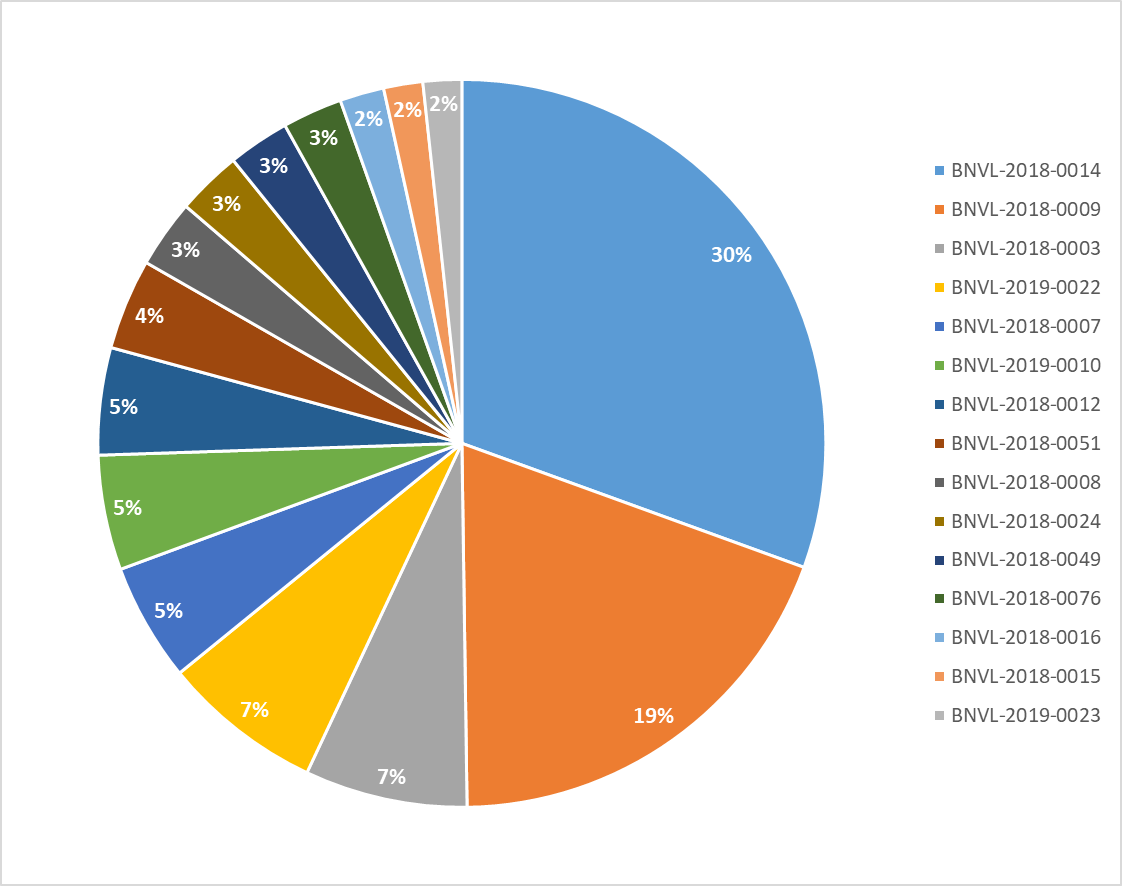
BNVL-2018-0014 and BNVL-2018-0009 are taking 49% part of this chart. They both WordPress-targeted attacks, but they are not the only ones in the Top 15 list. There are 3 other BNVL numbers, which connects directly to WordPress sites:
| BNVL number | Attack type | Number of attacks |
| BNVL-2018-0014
| WordPress Xmlrpc Scan | 76,107,969 |
BNVL-2018-0009
| WordPress Bruteforce Login Attempt | 47,953,676 |
| BNVL-2018-0003
| Testing for open form | 18,016,494 |
| BNVL-2019-0022
| PushDo/Cutwail Spam Botnet bruteforce | 17,765,617 |
| BNVL-2018-0007
| Automated WordPress Registration | 13,074,146 |
| BNVL-2019-0010
| Scan for open FTP server | 12,725,736 |
| BNVL-2018-0012
| WordPress username enumeration | 11,867,971 |
| BNVL-2018-0051
| Backdoor testing | 10,059,911 |
| BNVL-2018-0008
| Redirect Vulnerability in WordPress's WP Login Plugin (wp-login.php) (CVE-2014-2229) | 7,519,850 |
| BNVL-2018-0024
| BitNinja CAPTCHA request | 7,202,653 |
| BNVL-2018-0049
| Backdoor testing | 6,810,795 |
| BNVL-2018-0076
| Scan for Joomla! k2 content extension | 6,631,478 |
| BNVL-2018-0016
| Testing for User Enumeration and Guessable User Account (OWASP-AT-002) | 4,894,999 |
| BNVL-2018-0015
| Joomla! Automated registration attempt | 4,338,098 |
| BNVL-2019-0023
| Chinese Spam e-mail intercepted by the BitNinja SMTP CAPTCHA module | 4,280,444 |
Attacking countries
Where all these attacks were coming from?
China is always the number 1 attacker country, but Egypt, Vietnam, Brazil and the US are also on the Top 5 list, where the most attack came from in 2019.
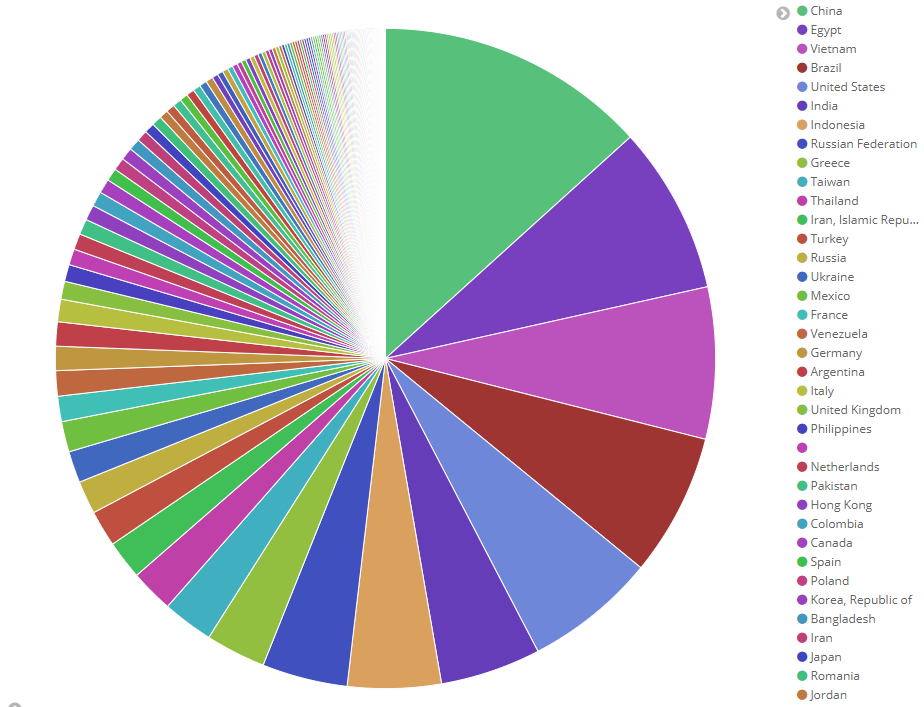
You can see on this map too, that which countries are responsible for the cyberattacks.
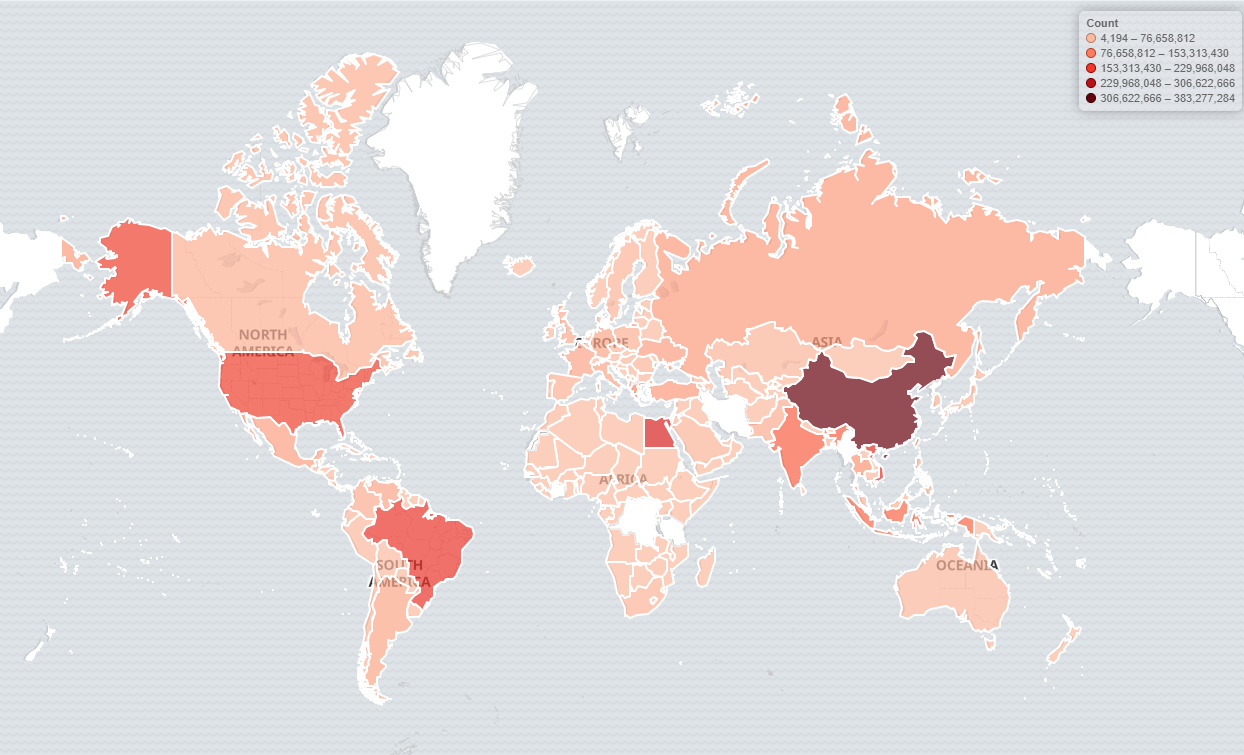
With BitNinja, you can block whole countries, however, it’s not always recommended. Instead, it’s more effective to block only malicious service providers
.
Inside our business
After reviewing the main events of BitNinja and the cyberattack trends, let’s talk about our business’ performance in a nutshell:
- The number of BitNinja protected servers increased by 55% in 2019
- We sent out 7,633,156 incident reports*. This means that are still a huge number of businesses out there, who don’t have the right security provided to their servers.
- The number of BitNinja partners increased by 95%. It’s a pleasure to us that we can keep all of these businesses safe.
- Our reseller partners were quite successful this year. Their share from the total MRR increased by 5% from Q3 to Q4.
- Customer satisfaction was increased by 95%. We reached 80 NPS**, while the industry average is only 60. Here are some of the feedbacks:
Easy to use. Beyond worderfull support. THANKS!!!
Simple brilliant at what it does.
BitNinja has rejected many attacks on my servers and I can recommend it even though I've only been using BitNinjaa one months. BitNinja will always be running on my servers! 🙂
Excellente tool against virus and others attacks
perfect security!!
I like bitninja because it's simple. I wish all security software was this simple.
We trust you and you have done well so far!! 🙂
I had to clean up my server, secure it, and prove my protection within 24 hours because of Abuse. BitNinja helped me in particular by visual representation of the attacks! Meanwhile, I do not need to worry about it anymore. BitNinja does it independently.
BitNinja is the best.
You got everything a client needs regarding security
Because it works better than any other solution i've found.
This is awesome! is the best antimalware software that i found.
It is the peace of mind having the hackers being turned away from our server.
Ease of use, listen to feedback, great team, Brilliant Product
cause its awesome and i can see live what its protecting and its affordable...
its just awesome. Far better than other products we've tested.
These were only a little part of all the wonderful feedbacks that we are receiving from our ninjastic friends from day-to-day. It’s a perfect motivation for us to keep going on this road and help even more people to secure their servers.
*When BitNinja perceives an attack from an IP, we inform the owner about this issue, because, in most of the cases, they don’t even know that their servers are infected and attacking other nodes.
**NPS=Net Promoter Score is purposed to measure customers’ overall perception of a brand.
Thank you for this awesome year
A lot of things happened and we reached unbelievable successes in 2019. We couldn’t have achieved all of this without our NINJASTIC partners. We love you guys. <3
Thank you so much for inspiring us every day to work harder and harder on the road to make the internet a safer place.
We promise you, that we don’t stop working such enthusiastically and 2020 will bring you many great news too. 😉















